

While verification and authentication are terms that are often used interchangeably, they are in fact two separate operations. Although they both work towards a mutual goal, they exist at different stages of the identity-checking process and use different methods for identity validation.
Digital verification and authentication play a critical role in preventing fraud and cyberattacks. Identity theft and data breaches are ever-present cybersecurity concerns, with Check Point research showing that cyberattacks are on a 50% increase per week.
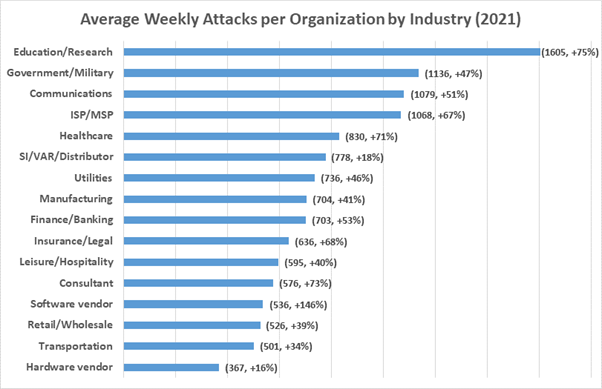

From business-wide encryption to cloud-hosted VoIP phone systems, businesses are implementing advanced technologies to achieve protection at every entry point. Digital verification and authentication technologies defend user entry points by verifying an individual’s claimed identity and ensuring that they, and only they, can access their account or resource.
What is Identity Verification?
Verification goes one step further than simply asking, “who are you?” This one-time process aims to validate a person’s identity, essentially answering the question: “are you really who you say you are?”
Once a user has identified themselves, the verification system will request information to verify their claims.
Verification helps to both deter and weed out criminals, mitigating the risk of fraud and data breaches. This in turn establishes mutual trust between the user and the system, as customers can be assured that the company is protecting their data.
While verification can be performed manually by humans, it’s a time-consuming process with a risk of human error. For this reason, businesses employ secure data extraction tools and advanced machine learning technologies. These digital solutions are much more reliable and are better for controlling inventory and providing fast and frictionless user experiences.
What are the Most Common Verification Methods?
The degree that a business invests in verification processes depends on its industry and business goals. Social media websites, for example, want to provide a streamlined onboarding experience and therefore tend to only require low-tier identity information like an email address, birthday, and phone number.
Government organizations, on the other hand, will employ much more extensive verification methods.
Here are some of the most common digital identity verification methods.
ID Document Verification
If you’ve ever tried to open a new bank account or take out a new car insurance policy, you’ll know that ID document verification is part of the onboarding process . The system will then scan and analyze it to determine its legitimacy.
ID document verification uses advanced artificial intelligence and authenticity algorithms to detect and analyze security features like watermarks, holograms, and fonts. It can also read the document’s information and validate it against third-party data sources. However, if an insurance company uses a legacy system (see “What is a legacy system in insurance?” for more info), the identity verification process may take longer as it will require more input from staff.


Image Source – Unsplash
Biometric Verification
Also popular with online banking, biometric verification is the method of using the applicant’s facial characteristics to verify their identity.
When prompted by the system, the applicant takes a selfie on their device. This has to be a high-quality picture that shows the applicant’s entire face.
Once the selfie is submitted, it’s analyzed using facial recognition technology. Biometric verification is used alongside ID document verification to help establish whether the person taking the selfie is the same person pictured in the ID document.
Database Verification
With access to various different data sources, database verification methods can help to verify an individual’s identity. The system will take the information submitted by the applicant and attempt to match it to the data found in the database. This could be an offline or private source, like Kudu database, or a public database like social media.
Poor verification implementation can have devastating results. As well as the financial loss, it can wreck your brand’s reputation, destroying customer trust and ruining partner relations management strategies.
What is Identity Authentication?
Verification is the process of proving your identity once in order to successfully onboard onto the system. Authentication is the process of proving your identity each and every time you try to re-access the system.
Authentication methods ensure that the person trying to access the account is the same person who signed up for it. Or, in the case of things like network security, it ensures that only authorized persons can access specific information.
Keeping authentication secure is critical to fraud prevention because it significantly minimizes the risk of unauthorized persons gaining access to sensitive information.
What are the Most Common Authentication Methods?
Much like verification, the methods used by businesses will vary depending on the level of risk and user experience goals.
The more secure the authentication type, the more tedious the sign-in process, which can lead to frustrated customers and poor internal practices. On the flip side, authentication methods that provide frictionless user experiences tend to be less secure.
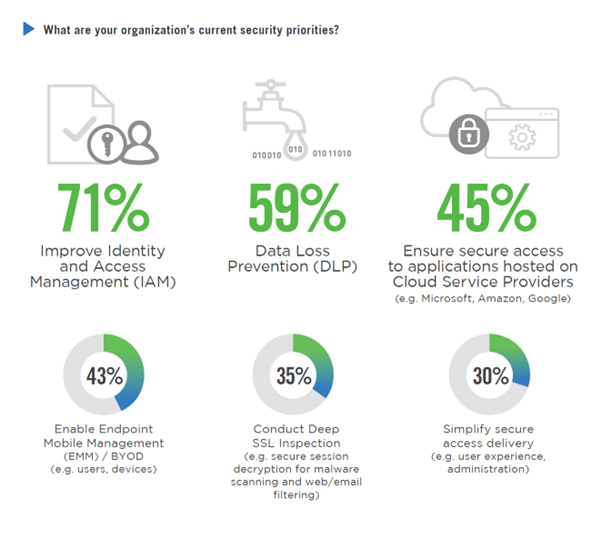
While balancing usability with security can sometimes feel precarious, remember that protecting data wherever it exists should be a top priority. Of all the security priorities, 71% of businesses agree that improving identity and access management is the most pressing concern.

The Username/Password Combination
The username and password combo remains the most widely-used single-factor authentication method thanks to its simplicity. Passwords can be a string of letters, numbers, and/or special characters.
Some authentication systems try to increase security by governing the strength of the password. For example, the system may only allow passwords of a certain length, or passwords containing at least one capital letter and/or special character.
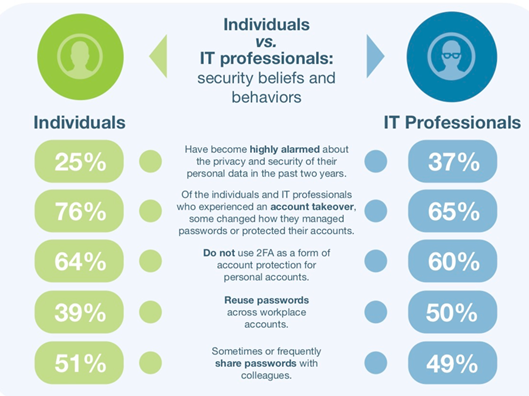
Despite this, passwords commonly fall prey to phishing, credential stuffing, and other malicious attacks. Poor password hygiene has a lot to do with this. The Ponemon Institute found that 39% of individuals and 50% of IT professionals repeat passwords across their workplace accounts. Other bad behavior included things like sharing passwords with others and failing to change passwords after account takeovers.

Two-Factor Authentication (2FA)
2FA strengthens single-factor authentication by adding a second step. It’s become a popular security solution for online services that host large volumes of sensitive data, such as virtual business phone number access or online banking.
After confirming their username and password, the 2FA system will ask for additional information. This is often a one-time SMS code that the system has sent to the user’s registered device, but it could also be a fingerprint or facial ID. Essentially, it is something that only the user should have access to, thus reinforcing that they are who they say they are.
Knowledge-Based Authentication (KBA)
KBA uses something that the user knows to authenticate their identity. This is usually the answer to a secret question that they provided when setting up their account. Typical questions include the user’s favorite holiday destination or the name of their childhood best friend.
KBA is a less-secure authentication method because the answers to these questions can be easy to guess or even found on social media accounts. For this reason, KBA is almost exclusively used as part of a two-factor or multi-factor authentication strategy.
Certificate-Based Authentication
This type of authentication technology can identify users, servers, and devices using digital certificates. Digital certificates are a type of electronic document or password that uses public key cryptography to authenticate identity.
Digital certificates can only be issued by a certificate authority. When a user attempts to log in using their digital certificate, the system will analyze the digital signature for its authenticity. It will also take the user’s private key and match it to stored information.
Certificate-based authentication is used in all types of network, software, and cloud security. Cloud integration platforms, like SAP cloud platform integration suite, allow you to enable certificate-based authentication alongside other authentication methods to achieve multi-layered security.
Biometrics
Biometric authentication validates unique biometric characteristics against the information that they received during verification. For example, if a person verified their identity with their fingerprint, they can then authenticate their identity in the same way. Other biometric technologies include iris scanners, facial recognition, and voice recognition.
The Key Similarities and Differences Between Verification and Authentication
The key similarity between verification and authentication is that they both use digital technologies to establish a user’s identity. Both are critical to preventing fraud and cyberattacks, and play a key role in building customer trust.
However, the two identity-checking methods have fundamental differences that are summed up in the table below.
| Verification | Authentication |
| Aims to verify a user’s identity for the first time. | Aims to verify that the user trying to access the system is the same user who registered. |
| Usually only takes place once. | Takes place every time a user attempts to access a system or resource. |
| Uses physical government-issued documents to verify identities, such as passports, ID numbers, and driving licenses. | Uses knowledge and access-based methods to verify identities, such as passwords and digital certificates. |
Wrapping Up
As cybercriminals grow smarter and identity fraud grows more pervasive, digital identity verification and authentication technologies are maturing to protect online data.
Verification establishes a link between the person’s claimed identity and their real identity. It uses increasingly intelligent technologies to analyze the authenticity of digital documents.
Authentication proves that the person trying to access the system is the same verified user. Both processes deter and combat malicious activity.
Many of our trusted business operations are migrating to the cloud. As we embrace paperless offices and switch from traditional to virtual IP PBX software, it’s vital that businesses leave no entry point undefended. Make sure that you’re continuously scrutinizing and reinforcing your identity-checking processes alongside your other cybersecurity measures.
Bio:
Tanhaz Kamaly – Partnership Executive, UK, Dialpad UK
Tanhaz Kamaly is a Partnership Executive at Dialpad, a modern cloud-hosted multi-line phone system for businesses that turns conversations into the best opportunities, both for businesses and clients. He is well-versed and passionate about helping companies work in constantly evolving contexts, anywhere, anytime. Check out his LinkedIn profile.



















