Hunting
HUNTING FOR NETWORK SHARE RECON
This post was originally published here by Matthew Hosburgh. There’s a strong chance you know what your organization is trying to protect. In many cases, this is probably in the form of data. It could be customer data, trade secrets, and forms of classified information. This data can be stored in many places: databases, email, […]
HUNTING MISBEHAVING POWERSHELLS: EXAMINING NETWORK PATTERNS
This post was originally published here by Matthew Hosburgh. Introduction By now the world has learned about the massive breach that Equifax reported in early September. The Cyber Kill Chain would classify the final stages of this attack as the actions on objective. Unfortunately, Equifax did not detect this activity in time to contain or prevent the data loss. […]
Exploring the Origins of Threat Hunting
This post was originally published here by Sqrrl Team. Threat hunting is one of the fastest-growing information security practices today. But what really defines threat hunting and how did the practice start? Recently, Sqrrl partnered with Richard Bejtlich from TaoSecurity to bring together a panel discussion comprised of the original General Electric CIRT incident handler […]
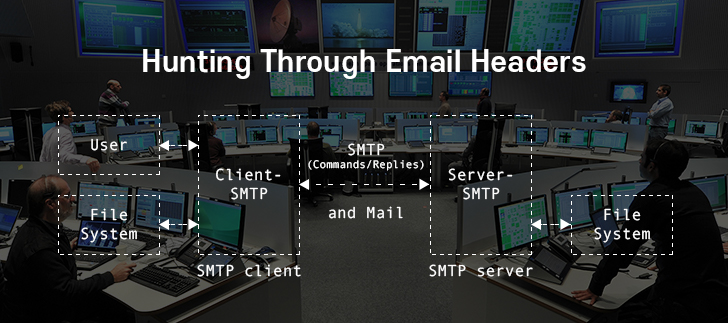
Threat Hunting Through Email Headers
This post was originally published here by Hem Karlapalem. The art of Threat Hunting can be especially fun when dealing with isolated individual pieces of puzzle. This article brings out the importance of email header analysis and how it can help in a hunt trip. Email header analysis is one of the oldest techniques employed […]