Sqrrl
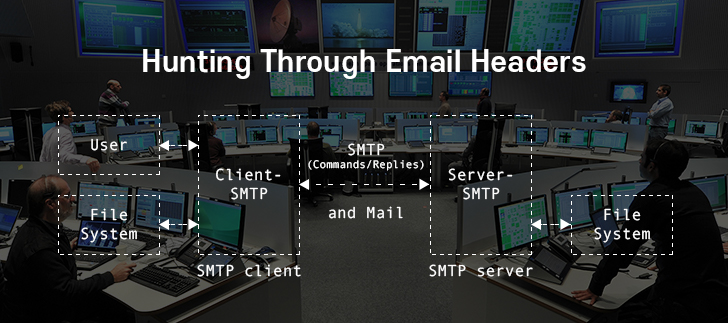
Threat Hunting Through Email Headers
This post was originally published here by Hem Karlapalem. The art of Threat Hunting can be especially fun when dealing with isolated individual pieces of puzzle. This article brings out the importance of email header analysis and how it can help in a hunt trip. Email header analysis is one of the oldest techniques employed […]
Arm Your Threat Hunters with Self-Service Analytics
This post was originally published here by Sqrrl Team. The new Sqrrl Enterprise 2.8 introduces an enhanced risk framework and powerful new analytic tools to simplify, accelerate, and amplify threat hunting. The new framework empowers analysts to create their own custom-built threat hunting analytics (“risk triggers”) without having to write any code. The extensible framework also now […]
How Attackers Lay the Groundwork for Lateral Movement
This post was originally published here by Ryan Nolette. The Hunter’s Den blog series aims to go beyond framework and theory and dig into practical tips and techniques for threat hunting. In our previous post, we examined the practical ways to hunt for C2 activity. In this series of posts, we will take a look at how to […]
The Hunter’s Den: Lateral Movement Part 1- Understanding Lateral Movement
This post was originally published here by Sqrrl Team. The Hunter’s Den blog series aims to go beyond framework and theory and dig into practical tips and techniques for threat hunting. In our previous post, we examined the practical ways to hunt for C2 activity. In this series of posts, we will take a look […]
Why do You Need a Hunt Team? The Answer May Surprise You!
This post was originally published here by David Bianco. You’ve probably heard this a million times now: “You need a hunt team”. This is true, as far as it goes, but why? For most people, the initial answer is probably something close to this: “So we can find bad guys on our network”. Again, this is […]
Threat Hunting for Command Line Process Execution
This post was originally published here by Chris Sanders. Processes are executed on systems in a variety of ways. A process might be executed by a user double-clicking an icon, by an automated service running at startup, or by a script referencing a third-party application. While not every attack requires the use of malware, most […]
Cyber Incident Investigation Series: Investigating Attack Scopes
This post was originally published here by Chris Sanders. As defenders, the critical moment is when we’ve determined that an attacker’s attempt to gain a foothold onto the network was successful. This sets of a chain of investigative activity where we follow breadcrumbs through our data to understand where they attacker went, what their mission […]
Cyber Incident Investigation Training: Reducing Evidence Abstraction
This post was originally published here by Chris Sanders. An incident investigation will only go as far as the evidence allows it. Of course, there’s a lot of components that have to come together to make that happen. The network must support the collection of robust and diverse evidence sources and it must be searchable […]
Answering Questions Before They’re Asked
This post was originally published here by Chris Sanders. Investigations are all about iterating through evidence that helps you make decisions about what events transpired on your network. That sounds easy enough, but asking the right questions and identifying the data you need to answer them is tricky. This problem manifests in two ways. First, […]
Retracing Investigation Steps
This post was originally published here by Chris Sanders. Finding evil is all about asking the right questions, finding answers, and using those answers to ask more questions. Each question and answer represent a decision point, branching the investigation off down a new path. The path of the analyst is far from linear, and sometimes […]