Threat
Kaspersky Lab signs Cyber Threat Intelligence agreement with Interpol
Kaspersky Lab has decided to raise its commitment towards fighting cybercrime and so has signed a Cyber Threat Intelligence agreement with INTERPOL. And according to sources reporting to our Cybersecurity Insiders, the agreement is designed as a legal framework to facilitate and develop cooperation between Kaspersky and Interpol by sharing data related to threat intelligence […]
Chinese hackers launch Cyber Attack on Australian Defense Contractor
A Chinese hacker or a hacking group named ‘Alf’ is said to have launched a cyber attack on an Australian Defense Contractor to access critical info about the nation’s defense secrets. Australian Federal Minister Dan Tehan has confirmed the news and said that the hacker/s had access to the network of the contractor for an […]
Exploring the Origins of Threat Hunting
This post was originally published here by Sqrrl Team. Threat hunting is one of the fastest-growing information security practices today. But what really defines threat hunting and how did the practice start? Recently, Sqrrl partnered with Richard Bejtlich from TaoSecurity to bring together a panel discussion comprised of the original General Electric CIRT incident handler […]
Kaspersky Security Software of Russia to be banned in the United States
Use of Kaspersky Security Software in government agencies of United States will now on be banned as per a new law formulated by House Science Committee. And according to the details available to our Cybersecurity Insiders, usage of the said security software has already been restricted in 22 US government agencies which include General Services […]
Threat Hunting for HTTP User Agents
This post was originally published here by Chris Sanders. An attacker will use the minimal amount of effort required to compromise your network. That means when it’s possible to reuse applications, tools, and protocols…. they’ll do it! This is one reason why attackers often use HTTP to facilitate communication to and from infected hosts. In […]
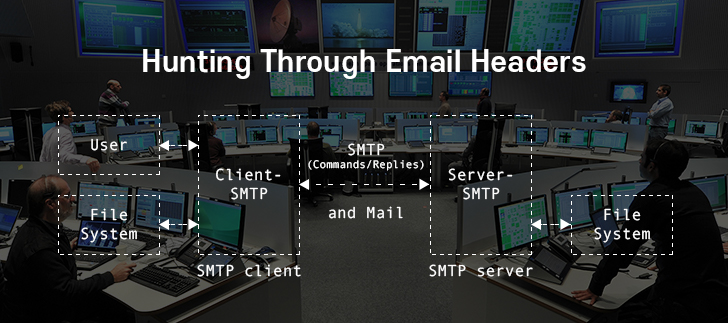
Threat Hunting Through Email Headers
This post was originally published here by Hem Karlapalem. The art of Threat Hunting can be especially fun when dealing with isolated individual pieces of puzzle. This article brings out the importance of email header analysis and how it can help in a hunt trip. Email header analysis is one of the oldest techniques employed […]
Insider Threats are increasing due to BYOD trend!
A recently conducted ‘Insider Threat’ survey by DTex confirms that BYOD explosion is helping threat landscape increase in organizations across the United States. The security vendor also confirmed in its report that nearly half or 48% of the 400 IT pros participating in the survey have confirmed that detecting and mitigating insider threats is becoming […]
Arm Your Threat Hunters with Self-Service Analytics
This post was originally published here by Sqrrl Team. The new Sqrrl Enterprise 2.8 introduces an enhanced risk framework and powerful new analytic tools to simplify, accelerate, and amplify threat hunting. The new framework empowers analysts to create their own custom-built threat hunting analytics (“risk triggers”) without having to write any code. The extensible framework also now […]
Filling in Threat Detection Gaps: a Q&A Interview with Danny Akacki
This post was originally published here by Sqrrl Team. Danny Akacki currently works as part of a hunt team at a Fortune 100 company in the financial sector. He started threat hunting at Mandiant as part of David Bianco’s team, and has spent the past four years working in threat hunting and incident response. Key Takeaways: Embrace “purple […]