Outpost24
Container Inspection for Cloud DevOps
by Sergio Loureiro, Cloud Security Product Director at Outpost24 Containers have become very popular with DevOps as a way to increase speed and agility. However, with hackers utilizing vulnerabilities in Docker container images to compromise hosts and launch malicious containers – how to identify this at the time of development and prevent security costing you […]
Ransomware Attacks Can Be Prevented, Really
Ransomware is a serious security threat affecting companies of all sizes and industries. While the symptoms (an attack) can be extremely damaging and disruptive, the solution can be simple – proactive prevention through a heavy dose of security hygiene. Here we cover the basics of Ransomware and top tips for securing your organization against it. […]
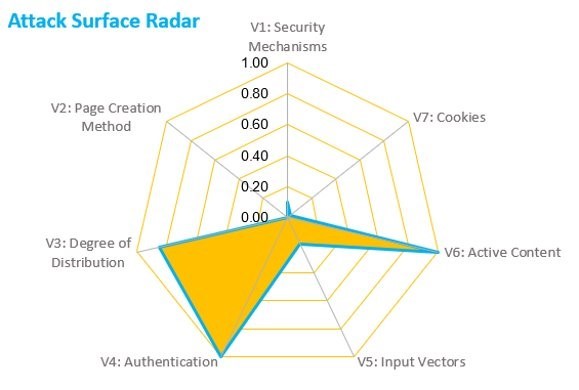
The 7 Deadly Vectors – Debunking the Elusive Web Application Attack Surface
Complex is a term that is often used to describe the technological make up of modern web applications. They are like onions, made up of intricate layers where, if not designed or secured appropriately, can foster many critical vulnerabilities. In fact, successful web application attacks pose a serious threat, as they account for almost half […]

















2024 is Here: Will This Be the Year We Get Passwords Right?
[By Darren James, Senior Product Manager, Outpost24] Humans have made unbelievable advancements in science and technology that have stretched the imagination and changed society forever. But one seemingly mundane, albeit crucial, piece of wisdom continues to elude mankind – proper password management. We’ve all seen the headlines about the next big breach, the majority of which […]