
Enterprises have made heavy investments in their own Security Operations Centers (SOC), or in SOC services delivered by Managed Security Service Providers (MSSP), but breaches seem to be occurring more frequently, and with greater consequences.
According to IBM’s 14th annual Cost of a Data Breach Report, between July 2018 and April 2019, the average total cost of a data breach reached US$3.92 million, and took a record-breaking average of 279 days to detect and contain.
$3.92 MillionAvg Breach Cost |
279 DaysAvg Breach Lifecycle |
Breaches caused by malicious or criminal attacks were the most common, the most expensive, and the hardest to identify and contain. However, the report shows that organizations with fully deployed automated security solutions were able to dramatically reduce time-to-containment and costs for all breaches, including hard-to-detect malicious attacks. The effectiveness of these solutions rests largely on their adroit use of machine learning and advanced analytics to keep pace with evolving cyber threats.
A New Strategy: Network Traffic Analysis
Network Traffic Analysis (NTA) is an important new arrival among such intelligent, automated solutions. It employs a novel strategy – shifting threat hunting from perimeters and endpoints to network flows – and a smart use of advanced analytics, namely intelligence from deep packet inspection (DPI), to reveal threats via behavioral abnormalities in the way devices, data, applications and users interact.
NTA has built an impressive track record to-date of identifying hard-to-detect threats in near-real time – instead of months or even years. This success has prompted much industry interest, as evidenced by the first-ever 2019 Gartner Market Guide to Network Traffic Analysis.
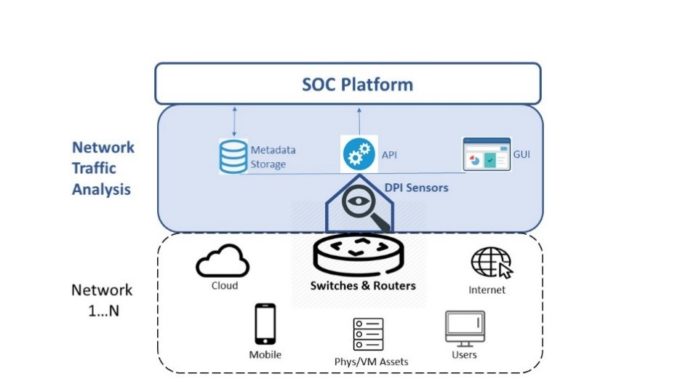
NTA & DPI Sensors
NTA works by deploying smart sensors alongside network switches and routers. Each sensor non-intrusively copies data from passing traffic. It uses this data to identify and classify protocols and applications, and generate rich metadata that that can be analyzed in real time for contextualized alerts, as well as stored for forensics and advanced analytics.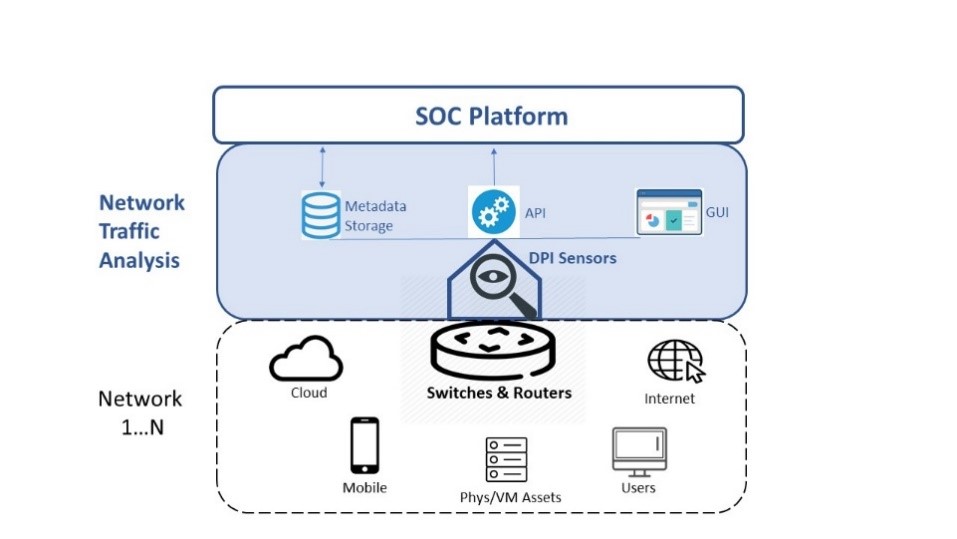

Qosmos NTA Sensor (DPI Probe)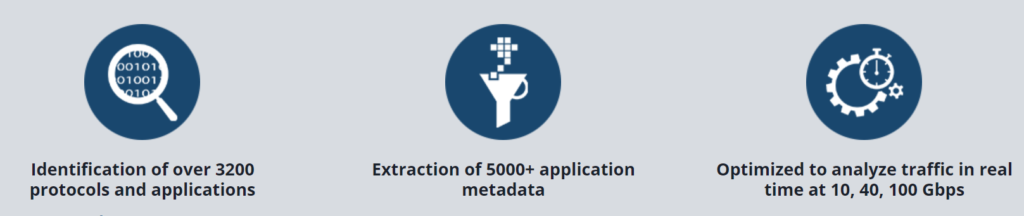

The Advantages of DPI-Based NTA
DPI-based NTA addresses three fundamental challenges facing today’s SOCs:
- Lack of Visibility: Footprint, Flow & Content Blind Spots
Outside of decryption (for which the window is closing), organizations have limited tools that can help them detect threats which have bypassed perimeter and endpoint defenses. NTA addresses this weakness by effectively profiling and classifying traffic without decryption, by detecting abnormal east-west/lateral traffic, and by enabling L2-L7 visibility into network activities. What’s more, NTA’s use of raw telemetry data evades the tampering that can occur with log files and endpoint instrumentation.Organizations also have limited visibility across the full scope of devices and systems that make their network. Software DPI sensors are easy to deploy anywhere in a network, and can be used for the inventory and localization of all services (assets) running on the infrastructure (whether physical or virtual).
- Inefficiency: Too Much Data, Too Few Hands
The volume of data SOC operators must sift through – emails, reports, files, alerts – increases exponentially almost daily. And it is a challenge that is sure to intensify as 5G is rolled out.At the same time, most organizations face a chronic shortage of skilled cybersecurity staffing. Research by Cybersecurity Ventures indicates this problem will get worse before it gets better, with 3.5 million cybersecurity jobs forecast to go unfilled globally by 2021. NTA addresses this labor/data challenge by enabling SOC staff to weed out low- or no-value data (e.g., developing application blacklists/whitelists), to better qualify and funnel alarms, and to reduce data storage (fully contextualized metadata reduces the length of time full packet data needs to be stored, and requires 150x less storage capacity).
- Rigidity: Static Tools & Manual Processes that Can’t Keep Pace
As noted above, today’s networks are continuously evolving: cloud services, network configurations, users, apps, and devices are in constant flux. The tactics used by cyber criminals are constantly evolving as well, with new threats arising at a rate of 8 per second according to McAfee Q4 2017 data. In this environment, DPI-based NTA delivers much-needed agility. Rapidly-deployed sensors can provide 100% global visibility for even the most dynamic, eclectic network environments. In addition, protocol classification, metadata generation, and behavioral baselining & analytics can surface new, never-before-seen threats, and shadowy lateral movements that pass under the radar of conventional tools.
To learn more about how organizations like yours can benefit from DPI-based NTA, register for the upcoming NTA webinar “The Importance of Network Traffic Analysis (NTA) for SOCs”.





















