

With a majority of data security breaches coming from internal sources, and 59% of employees who leave an organization claiming they take sensitive data, it is imperative that organizations know that the access they authorize is being used for its intended purpose.
Unfortunately, many insider threat preventive measures fall short or just focus on one aspect of the program. Therefore, most solutions need to be be augmented with tools built specifically to capture, analyze, and alert on insider activity and behavior. Whether the risk comes from accidental or negligent behaviors, or deliberate, malicious actions, organizations must know about a threat in order to prevent a damaging incident.

Today we are reviewing Veriato 360, an employee monitoring software that provides visibility into the online and communications activity of employees and contractors. The solution is for companies that want to improve productivity, conduct critical investigations, or keep important data safe.
Veriato 360 creates a definitive record of employees’ digital behavior while on a physical desktop, a hosted application, or on a virtual machine—and provides organizations with the ability to see the context of user actions. The software includes rapid alerting and viewing of detailed, accurate and actionable data for use in insider threat and productivity reporting.
Full Visibility Into Employee & Contractor Activities
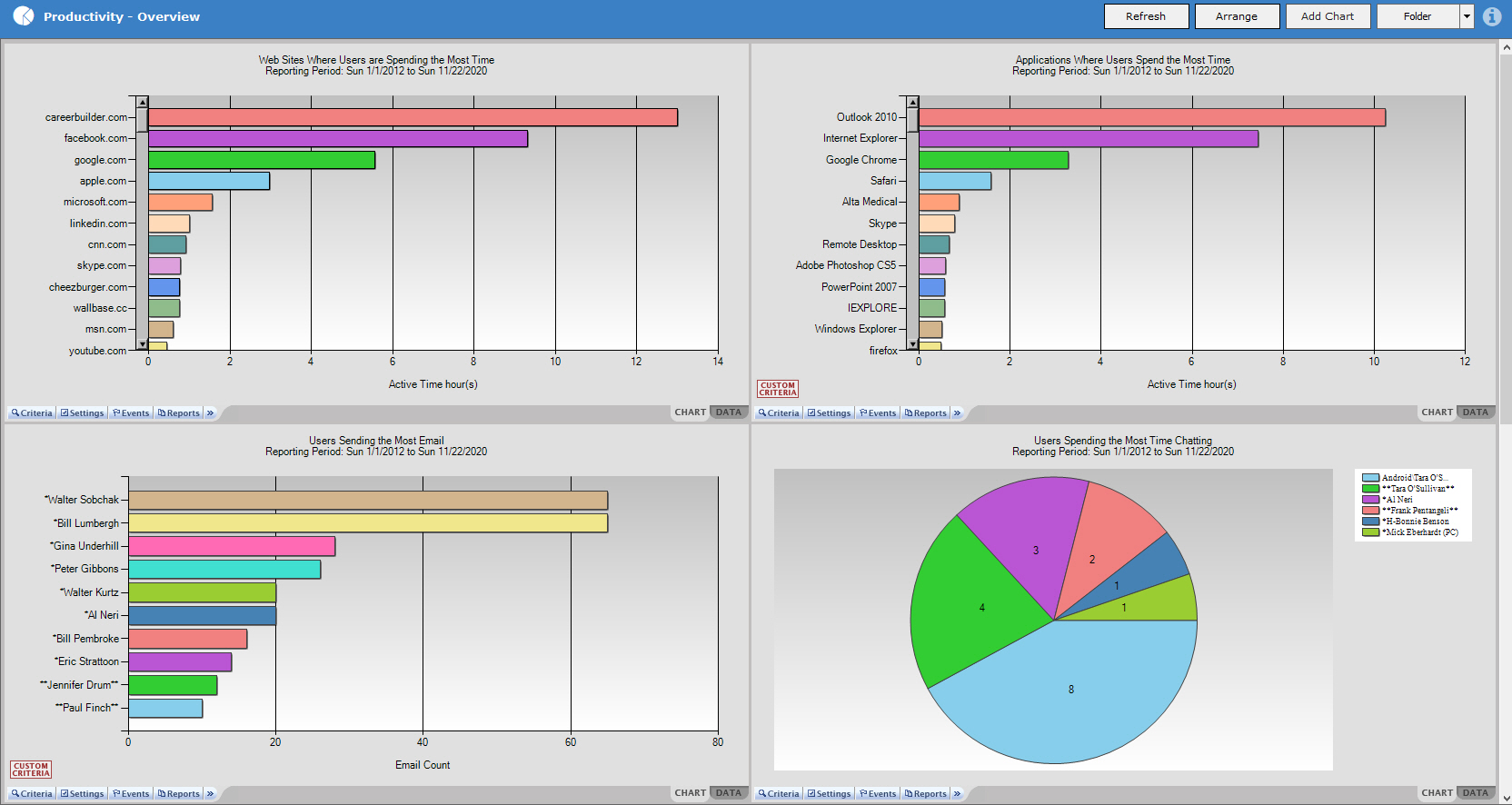
Veriato 360 offers organizations a way to gain an understanding of the size, scope, and severity of insider driven incidents, and to share that understanding quickly and effectively.
Each organization has its own triggers for what constitutes an insider threat and event. Veriato 360 gives organization full control and flexibility over what data is collected and when employees are monitored. The software collects and monitors full fidelity data on the activity of employees who interact with IT resources and information including web activity, file and application access, email and other communications. The Veriato keylogger feature, records all keystrokes, characters, and combinations to provide full transparency into the activity of highly privileged users. A single dashboard then presents these activities to enable security teams to identify activity patterns quickly.
![]()
![]()
The software includes the ability to conduct real-time, complex searches within specific activities or across all recorded logs as well. Security teams can also look backward at events to see if they overlooked any significant activities. For example, specific communication activities which were not initially deemed necessary to generate an alert on can be located quickly, efficiently and in context.
Never Get Caught Off Guard Or Wonder What Happened
It is no secret that higher risk employees require greater oversight. Veriato 360 provides detailed, context-rich, actionable data regarding user activity without interfering with workflow. Comprehensive reports allow security teams to quickly identify trouble areas involving intellectual property, data, network assets and employee productivity.
The solution tracks activities on local, removable, and cloud storage, as well as print operations. Then, activity alerting keeps security teams informed about potential security and policy violations, and can serve as a trigger to accelerate data capture when defined events occur. The software captures actual screen snapshots, replaying computer-based actions tied to activity data within context, before, during and after an event. Built-in and customizable alerts leverage detailed policies to identify troublesome activity within an organization’s perimeter. There is also a feature to create custom alerts that focus attention on problems pertaining a company’s most sensitive data.
In addition to the activity alerts, Veriato records all user data including tracking file movement, email communications, web activity, keystrokes, application usage, network activity, chat and IM allowing security teams know exactly what happened and when it happened. Captured data is written to an on–premises SQL database that uses a proprietary database schema. Object level encryption using AES or 3DES ensures captured data remains secure.
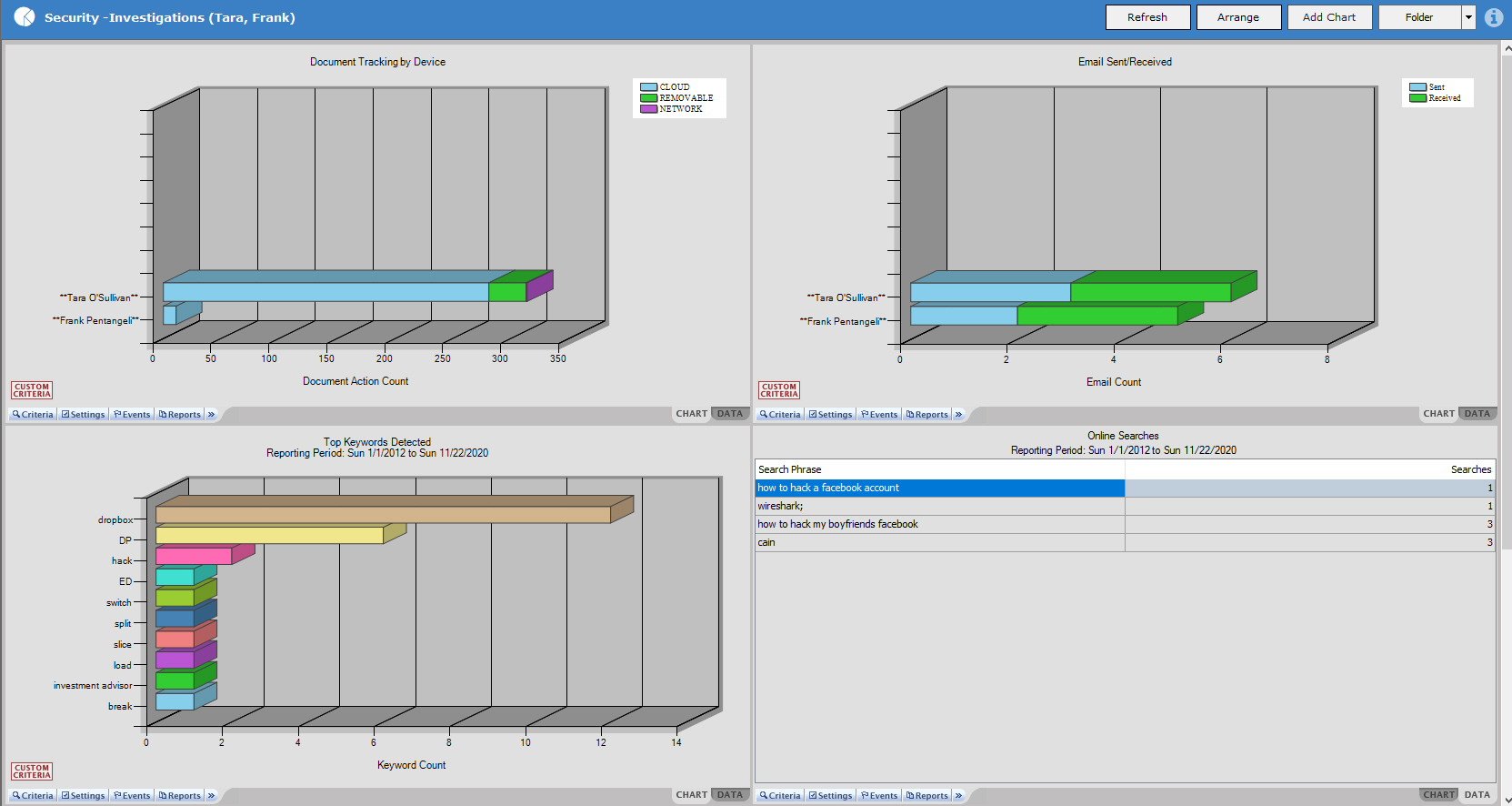

Conduct Thorough and Timely Investigations
Relying solely on the opinions of supervisors, without data to support their conclusions, introduces the potential for bias to creep in and for things to slip through the cracks. Having a system of record that clearly and dispassionately presents employee activity can, and does, improve the bottom line and helps sharpen decision-making. This is especially important in organizations that embrace telecommuting.
Veriato provides the analytic and real-time data investigators need to conduct a thorough and timely investigation. A DVR-like playback, intuitive search, quick view panels and scheduled reports minimize time spent getting accurate answers to support decisions.
The detailed record of all computer activity recorded by Veriato 360 allows investigators to zero in on the events that occurred quickly. Investigators can quickly and easily understand the “who,” “what,” “where,” “when,” and “why” of any incident and efficiently bring the incident investigation to an effective conclusion.
Proof Positive A Breach Occurred & Prevent One From Happening In The Future
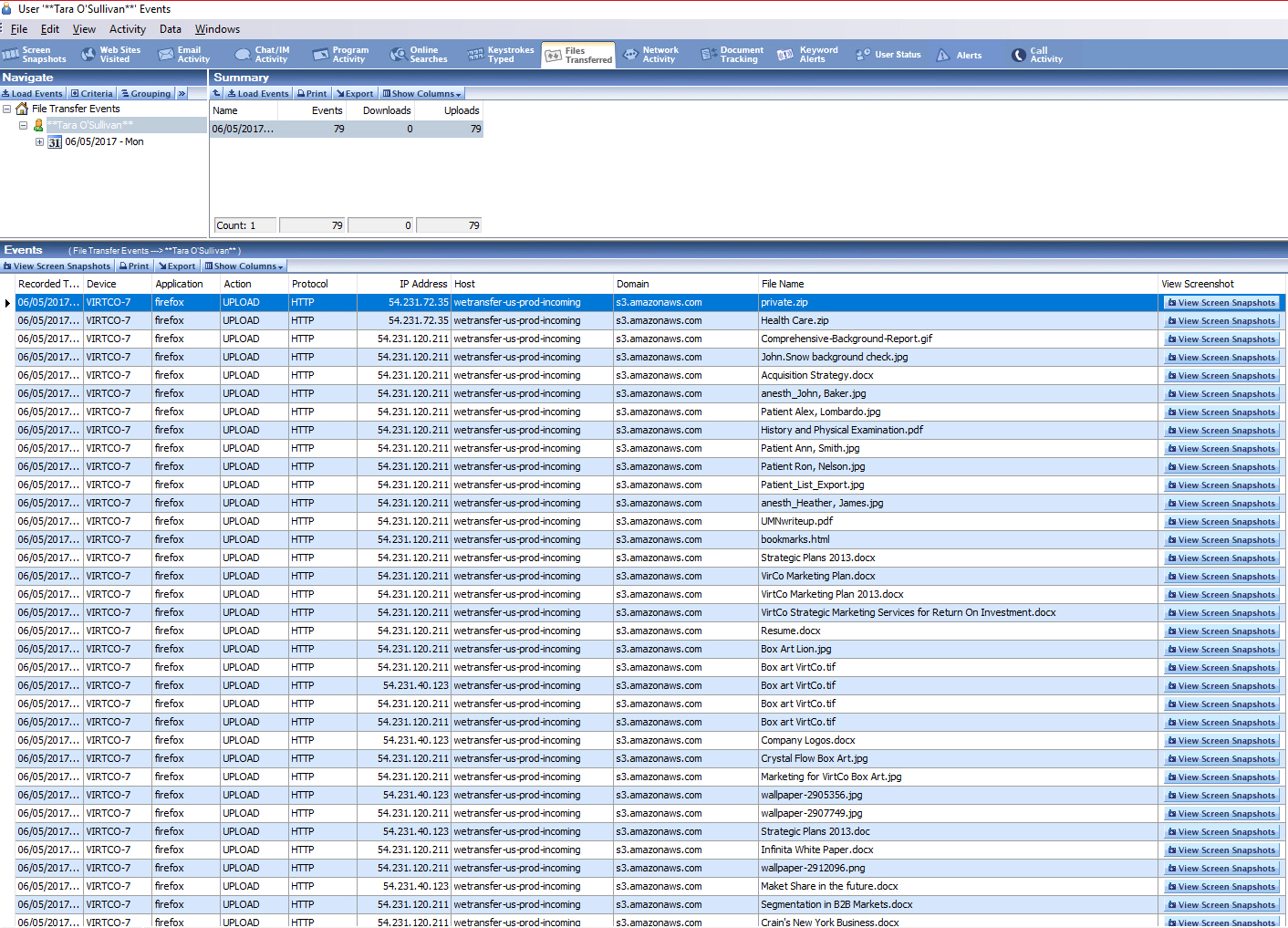
Veriato 360 screen recording and playback presents the activity exactly as it occurred and by whom allowing investigators to see when files were created, edited, deleted, or renamed. The solution also distinguishes between active and focused time providing the context to understand if an application or website was opened and left idle, or being actively interacted with. These detailed, user-by-user records of activities provides the necessary forensic data to quantify the potential impact of an identified incident.
Veriato 360 can, for example, quickly alert HR and security when an outgoing sales person attempts to download the company’s customer database – which could potentially be used by the individual to poach customers when they get to their new position. Using Veriato 360 the organization would not only be notified that the outgoing sales person is thinking about the data theft but would provide a detailed record of any theft. According to one customer, Veriato provided proof positive that an accused employee of cyberbullying wasn’t doing what his colleague said he was.

What Customers Say
“Since Veriato 360 worked so well for our customers, we decided to use it in our own office, and it has worked perfectly, For one thing, just the thought that their managers can see if they are working—and how they are working—is a huge deterrent to any wasteful activity. No more wasted time watching movies far beyond their break or checking social media throughout the day. Long-entrenched habits have changed quickly.”CEO, IT Services Company
Licensing, Pricing, & Deployment
Veriato 360 is delivered as software. Pricing is variable depending on total number of endpoints with special rates for government organizations and Managed Service Providers (MSP). The software is simple to install, and easy to put into practice and maintain. Veriato touts that it can be ready to use within hours. Support is delivered through it US operations – not outsourced overseas.
The software includes an intuitive setup that walks through the installation process. The Veriato Management Console provides the capability to find and select devices from Active Directory, Network Discovery, or an imported list and manage large-scale deployments for a single, simultaneous Recorder installation. Third-party technologies can also be used for recorder deployments. Organizations create multiple groups based on their needs. Devices are added to selected Recorder groups allowing the ability to follow their installation progress and manage licensing, recording policy, and version updates en masse.
A single, central user interface, enables the management, investigation, deployment and reporting of incidents. Reports provide high-level insight into user activity on an ad-hoc or scheduled basis; Veriato 360 ships with over 50 prepackaged reports plus the ability to create custom reports.
About Veriato
Veriato is an innovator in actionable User Behavior Analytics and a global leader in User Activity Monitoring. The company has over twenty years of experience creating user behavior monitor technology, and more than 40,000 companies, schools, and government entities worldwide utilize Veriato to gain insight into the user activity on their networks and benefit from the security and productivity increases that come with it. Veriato customers include 8 of the top 10 defense contractors, 8 of the top 10 technology providers, 7 of the top 10 financial services companies; and 6 of the top 10 healthcare providers and we are trusted in over 100 countries worldwide.
Veriato’s product line includes employee investigation tools ( Veriato Investigator), User and Entity Behavior Analytics (Veriato Recon), User Activity Monitoring (Veriato 360), and Ransomware defense ( Veriato RansomSafe).
Veriato has won multiple awards including Cybersecurity Excellence Awards within the Endpoint Security Category, TopTen REVIEWS Silver Award for Best Employee Monitoring Software and InterOp 2018 Award for Best Data & Analytics.
For More Information:
www.veriato.com
Toll Free: +1 888 598 2788
Email: sales@veriato.com




















