
This post was originally published here by Kristina Sisk.
What is your team hunting for in 2018? If you don’t know, how can you be sure you are positioned to safeguard your organization?
In the days of old, threat hunting was regarded as an ad hoc service for an organization. It is now an intrinsic part of an organization’s defensive posture and provides the organization the ability to be nimble and seek out threat actors in their environment based on the most recent attacker TTPs. Threat hunting has undeniable return on investment for an organization, but with threat actor dwell times still averaging in the hundreds of days, the investment matters more.
A Hunt Calendar
The premise of a Hunt Calendar is to provide your team and your leadership advance notice for targets in upcoming hunt operations. I have been planning my hunt team’s 2018 Hunt Calendar over the last few months. This calendar gives my team an iterative process to hunt with as well as add the ability to tack on hunts for high risk/priority TTPs as the year goes on.
Team
Before deciding the threats or the targets for your Hunt Calendar first consider the structure of your team. This is going to vary greatly based on the organization and the attributes and skills of your team.
Size
The largest constraint you are going to incur will be based upon the none accounted for man hours available to your team.
- What are your hiring projections for 2018?
- What is your current headcount?
- How are you freeing up your team to allow them to hunt?
- How many projects and roles are assigned to each member?
- Are they suffering from alert fatigue?
Talent
We all know there is a shortage of cybersecurity talent. This means that how you structure your team will likely be based off your recruiting strategy.
- Do you currently have “jack-of-all-trades” hunter or subject matter experts (SMEs)?
- Forensics
- Network
- Endpoint
- Malware
- Reverse engineer
- Detonation lab
- MAS (malware analysis system)
- Risk
- Business process risk assessment
- Operations process risk assessment
- Security controls visibility and gap analysis
- How well do your hunters know your environment?
- Is your topology and network diagrams up to date?
- How often do you update them?
- How is responsible for these updates?
- Do do you map out the network to validate your diagrams?
- Is your topology and network diagrams up to date?
- Forensics
Roles and Responsibilities
As a consequence of the historically ad hoc nature of threat hunting, it is common to see hunters wear many hats for their organization.
- Does your hunt team provide any other blue team support?
- If so, how would this impact a set schedule?
- Did you create defined roles and responsibilities for your team?
- If so, does your team structure evenly spread those roles and responsibilities.
- How do threat hunts roll their findings back into the security controls life cycle?
- Are threat hunts being leveraged by operations and security teams to improve their security posture and closing gaps in coverage?
For this example, I am going to assume the following team structure for a team of 11 hunters and huntresses.
- 3 Hunt Team Pods
- Alpha
- Bravo
- Charlie
- 2 Free Agents
In this example, each pod has one network and one endpoint SME, as well as a few junior analyst. The free agents are available to assist any pod, develop new hunt analytics and track down findings to validate evil and escalate to an incident response team.

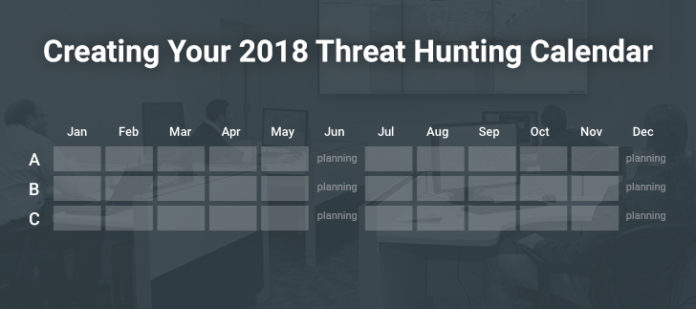
Given this structure the calendar looks a bit like the one below.
Consider providing your team two planning months. I have refined my planning process to use a bi-annual approach where we revise the entire calendar in either June and December or January and July. During the planning months, research your targets and the available hunting data sources. Begin any necessary relationships with teams that own the targets to ensure access to everything you need or take the time to finalize reports from your hunt operations.
Threats
What are the main threats to your organization and how do they present themselves?
- What threat actors have attacked your organization in the past?
- What tactics did they use?
- What assets did they attempt attacks on?
- What were they successful at?
- What keeps your CISO up at night?
- What were the trends last year and what is projected for next year?
- Numerous vendors offer white papers on these subjects, so go broad here.
- What geopolitical conflicts might make your organization a target in next year?
- Who are the main new threat actors in the landscape and what is their motivation?
- Where is your organization planning on going in the next 3 years and does that expand your threat landscape?
It is unlikely a hunt team will be able to cover all the identified threats. To prioritize your list, filter the threats down by considering what data sources already exist for the threats you face and how best hunting can support a larger detection strategy at your organization.
- Are you collecting authentication events?
- If not, how would you hunt for account abuse or compromise?
- Are you collecting East-West netflow traffic and not just North-South?
- If not, how would you detect lateral movement and internal reconnaissance attempts?
To keep this generic, we will say that you prioritize two nation states.
- Nation X is desperate due to increased sanctions and more of an unknown identity compared to other threat actors.
- Nation Y continues to remain highly invested in your industry. You choose an adversary that has targeted you before, APT Z.
Targets
If your organization has taken the time to identify critical assets, generally either for NOC support or as part of business continuity management, be sure to take those into account. If they don’t make good hunt targets, document why and what controls can be added to facilitate them in the future.
Putting it all Together
In the world of video games, role-playing games (RPGs) allow the player to level up the main character in multiple ways. You can grow your abilities to be strong in physical attacks or instead increase your magic abilities, but you can also choose a more middle-of-the-road approach. Every gamer knows there is no perfect character build, only what is right for the game you want to play.
Building a hunt schedule is similar to building a RPG’s main player capabilities. There is no one size fits all hunt schedule. Below is a middle-of-the-road example.
What does next year look like for Hunt Team Alpha?
Hunt Team Alpha starts off the year with an Adversary hunt operation. This hunt is focused on hunting for all the TTP’s of the attacker throughout the attack lifecycle. For this reason, I gave the operation an additional month compared to hunts focusing specifically on one target. Once that is complete, they have 2 months for a HVT hunt operation. From experience, I have decided that every hunt operation needs at least two months for a team size of 3 hunters, but this will depend on your toolset and the quality/accessibility of your hunting data.
In the second half of the year, Hunt Team Alpha has two more HVT hunts with a gap between them to work on new hunt analytic development or perhaps a team initiative developing a new tool. If you already know the dates of training or conferences for your team, the R&D block is perfect to schedule during this time.
In the example above, Hunt Team Charlie revisits HVT 3 at the end of the year after Hunt Team Alpha already did a hunt op in 1H 2018. For some targets, it may be pertinent to keep a hunt presence. A good way to do this is to hunt for different attacker tactics per op, like lateral movement in 1H and persistence in 2H.
Now What?
Once you create your schedule be sure to socialize it with key stakeholders and your leadership. If you haven’t had a headcount discussion for 2018 with your leadership yet, make two schedules; one with the current capabilities and one if you were able to get the headcount you are requesting next year. Similarly, you can use the schedule to justify a full-time hunt team, instead of a hybrid hunt and incident response team.























