
[ This article was originally published here by Indusface.com ]
Thinking about all the high-profile cyber threats that businesses face today can make you feel overwhelmed. The most devastating security breach incidents that made headlines, show the incidence of API abuse. Take Venmo, Panera, Equifax, WikiLeaks, and Uber’s hacks for example. With these incidents, it is clear that cybercriminals are becoming smarter, and many businesses are not focusing much on API security.
As our API-related development increases, so does the cybercriminals’ desire to take advantage of it – driving new evolutions in API security threats.
“By using APIs, companies may inadvertently open up the door to all of their corporate data,”
-Chris Haddad, chief architect at Karux LLC.
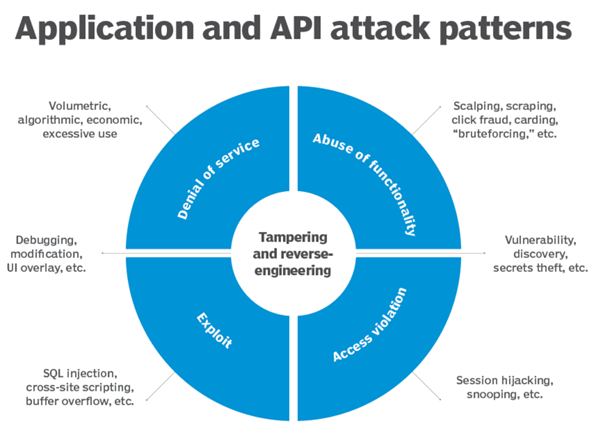

Source: Techtarget
So, how can you avoid becoming an API hack headline? The best way to leverage the power of APIs without confronting insider threats and external attacks is by following these API security best practices:
API Security Best Practices for Web Apps
- Implement A Zero Trust Philosophy
When it comes to “What is API Security?”, many people would highlight API authentication, but API security is more about API threat prevention. Zero Trust is a security policy centered on the principle that companies should not trust anyone by default and instead must verify everything trying to access their systems.
Zero-Trust ideology should be applied to even authorized API endpoints, authenticated clients, as well as unauthenticated and unauthorized entities.
Critical factors to consider while implementing a zero-trust policy on your API include API Protocol Support, API Deep Request Inspection, Cloud-native Deployment Method, API Discovery – Up to date API Inventory, and Data leakage prevention.
- Identify API Vulnerabilities and Associated Risks
It is dangerous to ignore API vulnerabilities and risks. Many API vulnerabilities and errors can be caught in the initial stage; hence, fixing them becomes easy and quick.
With thorough API security testing, discover which parts of your API are vulnerable to the known threats. Refer to the OWASP’s Top 10 API Security Vulnerabilities list to make sure the biggest vulnerability categories are mitigated. Also, identify all the data and systems that get affected if a vulnerability is exploited and create an appropriate recovery plan to reduce the risks to an acceptable level. Assess the API endpoints before any code changes to make sure any data handling requirements and security are not compromised.
- Enforce Strong Authentication and Authorization
Though authentication and authorization play different roles, when implemented together, these two API best practices work as a powerful tool for API security. Authentication is necessary for securely verifying the user of the API and authorization is concerned with what data they have access to. API authentication allows to restrict or remove users who abuse the API. API authorization usually starts after the identity is confirmed through authentication and verifies if users or applications have permission to access the API.
API authentication and authorization serve the following purposes:
- To authenticate calls to the API to legitimate users only
- To track the requesters
- Tracking API usage
- Enabling different levels of permissions for different users
- Blocking the requester who exceeds the rate limit
- Expose Only Limited Data
When we think of web API security best practices, we often think of blocking out malicious activity. It can also be helpful to limit the accidental exposure of sensitive information. As APIs are a developer’s tools, they often include passwords, keys, and other secret information that reveal too many details about the API endpoints. Make sure APIs only expose as much data as is needed to fulfill their operation. Further, enforce data access controls and the principle of least privilege at the API level, track data, and conceal if the response exposes any confidential data.
- Implement Rate Limits
DDoS (Distributed Denial of Service) is the most common practice of attacking an API by overwhelming it with an unlimited API request. This attack affects the availability and performance of APIs.
Rate limiting, also known as API limiting is a process of enforcing a limit on how often an API is called (to ensure that an API remains available to legitimate requests). Beyond DDoS attack mitigation, it limits other abusive actions like aggressive polling, credential stuffing, and rapidly updating configurations. API rate limiting not only deals with fair usage of shared resources but also can be used to:
- Implement different access levels on API– based services
- Meter the API usage
- Guarantee API performance
- Ensure system availability
- Implement Web Application and API Protection (WAAP)
We recommend a Web Application and API Protection (WAAP) solution for business use cases where API calls are made from the web and mobile apps. These apps commonly have access to ample amounts of sensitive information and APIs in these channels are tough to defend. Common security tools like traditional firewall and API gateway are insufficient to prevent API attacks. WAAP solution is centered around four consolidated capabilities: DDoS protection, Web Application Firewall, Bot Management, and API protection.
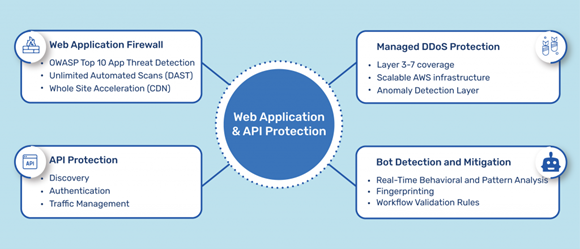

Source: Indusface
It employs a fully managed and risk-based application security approach by monitoring traffic to detect abnormal activities and malicious traffic across all four-vectors. With the data collected across all the applications, it assesses risks and updates the mitigation strategies to enhance cyber defense in real-time. WAAPs also aid to reduce operational complexity by reducing the number of parameters that need to be managed, streamlining security rulesets, and automatically suggesting rules with its AI capabilities. While WAF protects against OWASP top 10 attacks and API gateway defends against standard attacks, AI-enabled behavioral analysis of WAAP ensures the defense against automated and more sophisticated attacks.
Conclusion
As APIs become a strategic necessity to offer your business the speed and agility needed to succeed, your ultimate goal should be defending them from evolving attacks. These API security best practices for web applications may not be a fool proof strategy in enhancing API security but can go a long way in making your API’s protection tough to penetrate.





















