

“Ionut Arghire wrote an interesting post about DDoS Attacks Are Primary Purpose of IoT Malware that I would like to share.”
As the Internet of Things (IoT) market expands, the number of malware threats targeting the segment is rising as well. The ultimate goal for many of these IoT threats is to build strong botnets in order to launch distributed denial of service (DDoS) attacks, Symantec researchers say.
Compared to the record levels observed in 2015, when eight new malware families emerged, new IoT-focused malware appear to have decreased this year, although the security of IoT devices hasn’t improved much. These products are easy targets for cybercriminals and victims often don’t even realize they were infected.
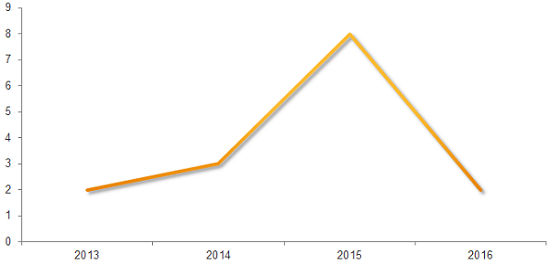
Chart: New IoT malware families by year (Source: Symantec)
Although these attacks were initially predicted to target the user, it appears that cybercriminals are interested in something else: using hijacked devices as part of botnets to launch DDoS attacks against various targets. In fact, most of the malicious applications built to target IoT can either launch DDoS attacks or can download malware that includes the functionality.
Over the past several months alone, researchers detailed DDoS incidents involving powerful botnets of IoT devices, including massive sustained attacks against properties and organizations affiliated with the Olympics. Thousands of CCTV devices worldwide were abused in similar attacks, and malware families such as BASHLITE and Linux/Mirai were observed actively ensnaring CCTV cameras, home routers and other type of compromised devices into botnets.
Just this week, security blogger Brian Krebs said that his site had been targeted in an attack that peaked at 665 Gbps, which he believes was powered by an IoT botnet.
According to Symantec, attacks that originate from multiple IoT platforms simultaneously might be observed in the future, mainly because more and more embedded devices are connected to the Internet. IoT malware, researchers say, mostly targets non-PC embedded devices, because they might not include advanced security features.
“Embedded devices are often designed to be plugged in and forgotten after a very basic setup process. Many don’t get any firmware updates or owners fail to apply them and the devices tend to only be replaced when they’ve reached the end of their lifecycle. As a result, any compromise or infection of such devices may go unnoticed by the owner and this presents a unique lure for the remote attackers,” Symantec says.
The security company also reveals that over one third of IoT attacks (34%) seen this year originated from China, with the United States following rather close at over one quarter of attacks (26%). Russia (9%), Germany (6%), and the Netherlands (5%) round up top five, followed by Ukraine, Vietnam, the United Kingdom, France, and South Korea (Symantec also admits that attackers might also use proxies to hide their real IP addresses).
IoT malware attempts to log into Internet-facing devices using pre-defined combinations of default usernames and passwords, the most common of which are “root” and “admin”. These combinations differ based on the targeted systems: when attacking Ubiquiti routers, the malware would use combinations of username: ubnt and password: ubnt, but it would switch to username: pi and password: raspberry combinations when targeting Raspberry Pi devices.
To infect IoT products, attackers scan for random IP addresses with open Telnet or SSH ports, when attempting to brute-force the device. Targeted platforms include x86, ARM, MIPS, and MIPSEL, and attackers compile their malware as cross-platform solutions, and even build variants for less used architectures, such as PowerPC, SuperH and SPARC.
“One interesting feature seen on a variety of IoT malware is the ability to kill other processes, specifically processes belonging to other known malware variants. In some older variants this feature might have been used just to eliminate the potential malware competitor from the infected device,” Symantec says. IoT malware might behave like this mainly to ensure the device’s resources aren’t used by other software.
Some of the most prevalent malware families targeting embedded devices includeLinux.Darlloz (aka Zollard), Linux.Moose, Linux.Pinscan / Linux.Pinscan.B (aka PNScan), and Linux.Wifatch (aka Ifwatch) –which don’t include DDoS capabilities –, along with Linux.Aidra / Linux.Lightaidra, Linux.Xorddos (aka XOR.DDos), Linux.Gafgyt (aka GayFgt, Bashlite) Linux.Ballpit (aka LizardStresser), Linux.Dofloo (aka AES.DDoS, Mr. Black), Linux.Kaiten / Linux.Kaiten.B (aka Tsunami), Linux.Routrem (aka Remainten, KTN-Remastered, KTN-RM), and Linux.LuaBot – which can launch various types of DDoS attacks.
Some of the threats that lack DDoS capabilities might still install DDoS-capable malware, researchers say. “DDoS attacks remain the main purpose of IoT malware. With the rapid growth of IoT, increased processing power in devices may prompt a change of tactics in future, with attackers branching out into cryptocurrency mining, information stealing, and network reconnaissance,” Symantec concludes.
—–
Source:
www.securityweek.com/ddos-attacks-are-primary-purpose-iot-malware
Photo: www.securityweek.com


















