

By Mark Wojtasiak, VP Portfolio Marketing, Research & Strategy, Code42
One year ago, an abrupt influx in remote work and collaboration tools changed the way we work, dare I say forever. With that came increased risks to company data — employees are 85% more likely to leak files today than they were pre-Covid, according to the 2021 Data Exposure Report. This data risk problem is the elephant in the room. Trailblazers like Rakuten are doing something about it — are you?
Why It’s Time to Redefine Data Protection with Insider Risk Management
The first step to solving a problem is naming it, and this one is called Insider Risk. Insider Risk is any data exposure event — security, compliance or competitive in nature — that jeopardizes the financial, reputational or operational well-being of a company and its employees, customers and partners. While this may sound like a marketing buzzword for insider threat, it is not. The distinction is that insider threat puts a magnifying glass on the employee, and insider threat tools like UEBA take a user-centric approach. Insider Risk Management solutions go beyond this by taking a data-centric approach that combines the three dimensions of risk — files, vectors and users.
Instead of a mere perception of protection that conventional DLP approaches create, an Insider Risk Management (IRM) approach to data protection prioritizes the tangible realization of value through measurable Insider Risk reduction. To help security teams accomplish this, this blog offers a pragmatic and realistic framework rooted in five core technical requirements.
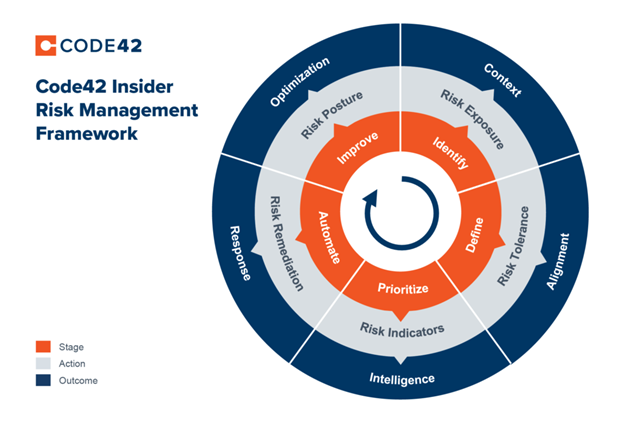

- Identify: It is crucial to have IRM technology in place that can monitor and identify the three dimensions of risk – file, vector and user – across all data, and is environment (Windows, Mac, Linux) agnostic.
- Define: Security teams must define trusted versus untrusted activities, scenarios and risk indicator severity to align on organization-wide Insider Risk tolerance and right-sized response.
- Prioritize: It is crucial that IRM technology can triangulate individual aspects of file, vector and user context to surface leading indicators of risk. This capability allows risk that comes with source code exfiltration, suspicious file type mismatches, syncs to personal cloud storage and departing employees to be surfaced above lower severity events.
- Automate: Automate a combination of human and technical actions to accelerate Insider Risk response. Because not all Insider Risk is malicious, response actions should be right-sized to the risk severity and situational context.
- Improve: Measure and optimize the organization’s overall Insider Risk posture and maturity by improving technology implementation and processes over time.
More and more organizations are looking to implement Insider Risk Management to detect and respond to data loss, theft and leaks. But, the biggest barrier to implementing or improving Insider Risk Management is designing the program itself. Forty-six percent of security leaders find defining the process and procedures to be the hardest part, and the reason why most organizations are reacting to Insider Risk more than they are managing it. This 5-step framework will help your organization address Insider Risk – and protect your data in today’s modern world.



















