

By Roark Pollock, Ziften Technologies
When the basics of infrastructure security go ignored or unchecked, much bigger problems will often occur. And attacks in the news over the past six months put this into clear perspective. This article takes into view into facets of ransomware and similar attacks from the perspective of the enterprise IT operations teams who control the edge. It lends perspective on why so many machines can become infected quickly. More importantly, how can enterprises behave differently and improve their stance to stop it from happening to them?
IT managers and security operations teams usually learn about data breaches and ransomware when a large-scale attack has been highly successful, such as the Equifax’s data theft through an unchecked server, or the Wannacry ransomware attack, siphoning money away from the organizations that are the victims. Many of these attacks demand $25,000 or more from the helpless victims who fear never seeing their data again.
According to a security professional survey conducted by the SANS Institute in June 2017, ransomware and phishing were the top 2 most significant threat to hit organizations over the past 12 months. With accelerated threats, visibility from the endpoint to the heart of the network operations center, along with automation tools that respond to attacks within seconds rather watching them spread across the infrastructure, make for a world of difference.
The State of Ransomware in 2017
The organizations targeted by Advanced Persistent Threats (APTs) has rapidly widened in the last 18 months. Popular at first were hospitals networks and health clinics, due to the sensitive mix of patient and financial data that is vital to all their daily operations. But today, insurance carriers, media companies, the broad financial sector, and manufacturers find themselves at the mercy of the hackers. Older ransomware names like Cerber and Locky have given way to even faster moving variants in 2017, such as Petya.
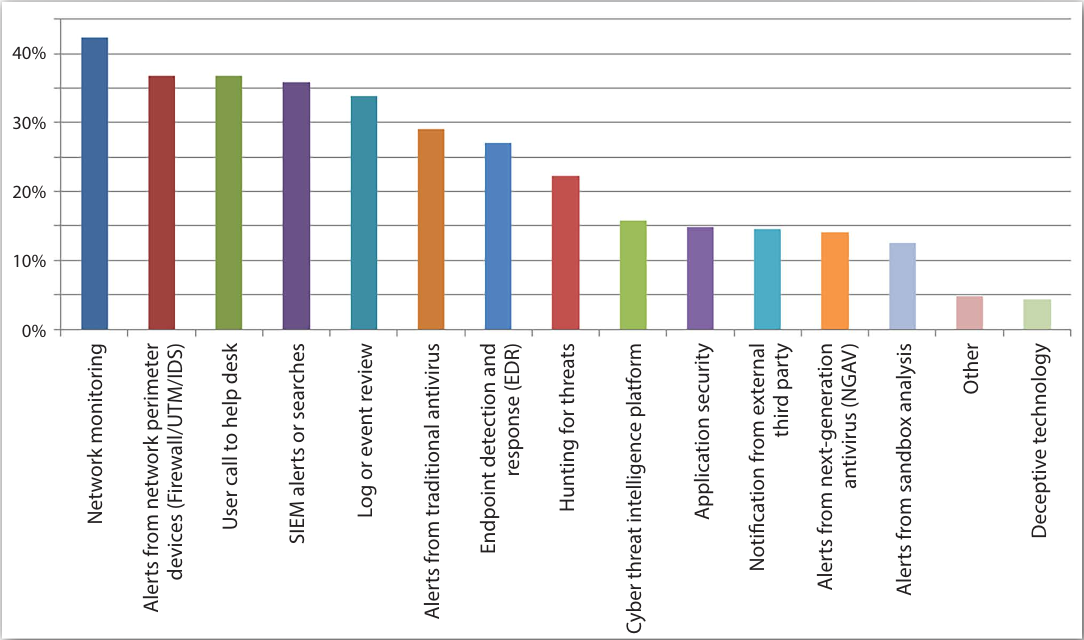
Fig 1. How were the most impactful threats discovered? [2017 SANS Institute Threat Landscape Survey: Users on the Front Line]
It starts with a vulnerability in the Information Technology (IT) infrastructure where users and devices are accessing data, it may be a batch of servers that have gone for years without updating, or through a phishing scam, with a hacker getting an employee to download dangerous malware code that establishes itself on a machine and then throughout links to other machines, where now the hackers have a way to encrypt files, or even to cause total data loss, erasing servers and drives all together. Bitcoin, the crypto currency is also key to the effectiveness of the attack. Asking for the money over an anonymous and failsafe system has made ransomware attacks not only lucrative, but rather easy to pull off without risk of detection.
Considering all this recent activity, the question is: are ransomware attacks just a passing phase that we will soon forget about?
According to Mike Hamilton, SVP of technology for Ziften Technologies of Austin, TX, “I don’t think ransomware is an anomaly. I think it will continue to get worse. And new strategies are required that go deeper into realizing what is happening across an IT infrastructure, seeing and reacting when things are changing. Most importantly, all of this must occur within seconds – not within days.“
Visibility that Creates a Baseline
Most enterprises have very little in the way of a holistic view of systems and devices, instead, they have to assemble islands of information from disparate sources, such as a security appliance, or a log of user calls, corresponding IP addresses, stemming from issues that have been brought into IT department. This becomes ad hoc at best, and does not allow for proactive monitoring of malicious activity due to the number of gaps and inconsistencies.
The importance of visibility and monitoring the network stand out.
In fact, according to the SANS Institute 2017 Threat Landscape Survey, “When it comes to discovery of threats with significant impact, network monitoring and alerts from the perimeter defenses are the top two means of discovery, followed by user calls the helpdesk.”
For a truly effective level of protection against ransomware attacks, enterprises need greatly increased visibility and control into what is happening across the entire scope of their infrastructure. They must unify their systems under one umbrella.
This means an endpoint management system that reaches everywhere, and continuously goes about collecting and reporting information about users, processes, binaries, server patch levels, and current status from any networked resource, at the physical edge, in the cloud and even in virtual machine environments.
All of this is necessary so that a baseline profile can be established from having a complete and holistic view of the systems. From there, security issues, compliance issues and operational issues can be accurately identified.
The Role of Patching
Patching servers, or even web browsers and operating systems has been a basic housekeeping function of enterprise IT, it works to an extent to keep the most secure software on all operating systems (OS) that connect to an internal network.
But patching is all too often a slow process that leaves networks vulnerable. To explain, we can examine a typical patching timeline:
- Week #1- A security hole is discovered and two weeks later the big vendor, such as Microsoft, issues its patch for all licensed users to download free of charge.
- Week #2- There are multiple days or even weeks between that patch getting issued and when enterprises actually implement the patch. When they do actually implement the patch, it first goes to a small test group to ensure stability of software. IT ensure the patch goes through to the next group.
- Week# 3- A larger test group has the patch pushed to them, checks are made.
- Week #4- Finally, the patch goes widespread to hundreds of devices, IT listens for the results in the form of user complaints or down servers. Before anyone realizes, a month has passed since the patch is issued and only then is it going enterprise wide.
In the immediate wake of a ransomware attack, one method is to disable SMB file sharing services entirely, until all systems have patches updated. This way, ransomware is frozen from infecting every reach of the network.
Patching is just one small part of the picture, but won’t solve the problem of endpoint protection.
A Better Answer – AV or ADR?
What about classic Anti-virus (AV) that security operations teams know so well since the 1990s? AV is the most widely deployed, and classic “signature” type security that solves some problems but has not been able to stop ransomware attacks. This is because new forms crop up within hours that have no signature and then rapidly snake their way through networks.
Automating Analysis
The emphasis on visibility into endpoint behavior is what is key to stopping the attacks, as the modus operandi for all ransomware is to begin encrypting files. When the EDR system can spot such activity, it then automatically stop it early. This is accomplished with pre-programmed actions that block the avenues which it spreads. Endpoint Detection and Response (EDR) is a vital tool in stopping ransomware. As it delivers attack detection, prevention and remediation.
Conclusion
Key to establishing an effective enterprise security foundation in the fight against ransomware is providing the heightened level of visibility and control concerning all connected systems and devices. Next is finding better ways to execute on the “blocking and tackling” of day to day security implementation, from device patching to reviewing forensics. And lastly, establishing a way for both IT teams and Security Operations teams to cooperate as one. EDR is one key piece of the puzzle, while shifting IT and Ops culture is the other.















