

Effective threat detection requires accurate forensics information for security analysts to make sharper and faster decisions. The quality of forensics output is heavily dependent on the data that is available, both in the form of logs and in the form of traffic intelligence. The more detailed the traffic visibility, the richer and more accurate the information available to analysts, which significantly improves detection and investigation.
A Deep Packet Inspection (DPI) sensor can strengthen network forensics capabilities without disrupting security operations, since it works transparently on a copy of the network traffic. In addition, a sensor can monitor internal and inter-VM traffic, which is typically out of reach for firewalls and network equipment. Integrated into existing security tech stacks, it complements threat hunting tools by leveraging the granular visibility of DPI to improve threat analytics.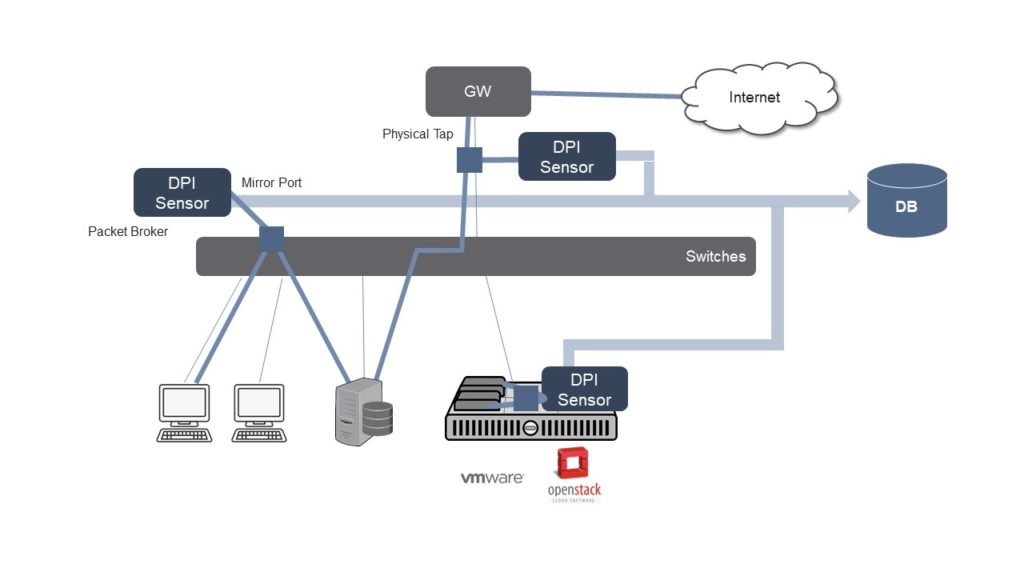 Figure 1: DPI integration in enterprise networks
Figure 1: DPI integration in enterprise networks
How Does It Work?
DPI is a proven technology, already widely used in cybersecurity to detect and mitigate threats. It is embedded in NG firewalls, UTM, secure gateways, and different types of threat analysis tools to ensure rapid and reliable detection of malware attempts and security breaches.
Used as a complement to traditional network security solutions, a DPI sensor is an expert tool for network forensics. Deployed by large SOCs operated by high-end MSSPs and Managed Detection & Response (MDR) service providers, it helps to streamline investigations and improve time-to-threat detection by delivering forensically relevant, detailed traffic information. A DPI sensor captures and analyzes 100% of traffic in real-time, and classifies it into organized flows, describing the protocols and associated metadata (actions or behaviors taken inside the session). Analysis should ideally include traffic shape (volumes, origin and destination, device type/VM, etc…) and content (queries, DNS requests, URLs, cookies, sender, receiver, attachment name, encapsulated traffic, etc…). The DPI sensor converts the network streams into SIEM-compatible syslog messages that can be used by the event collector. The event collector filters and aggregates the data, forwarding any critical events to the SIEM for alerting.
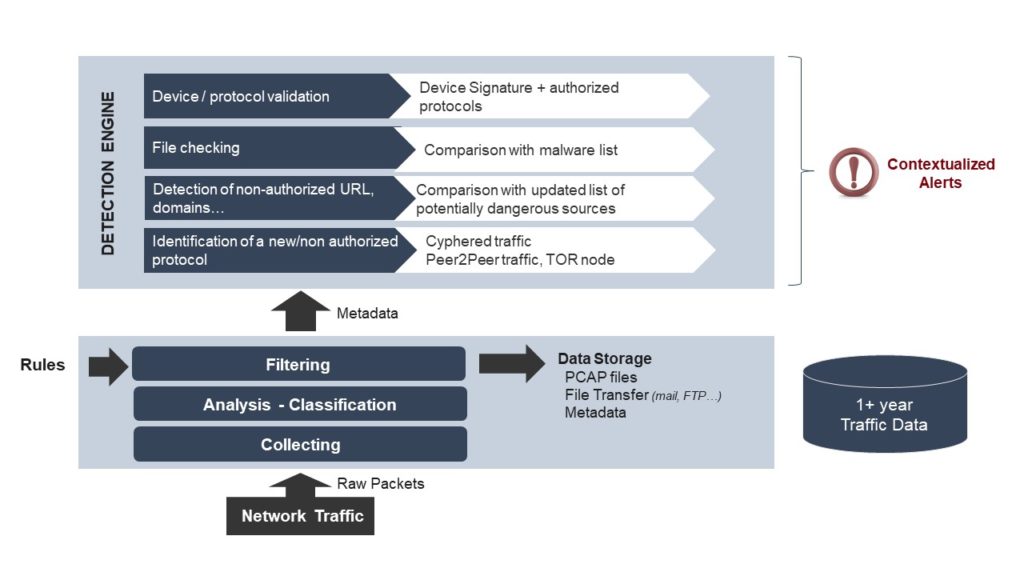

Figure 2: Examples of detection made possible with DPI sensors
Speeding and Improving Threat Investigations
When analysts investigate an alert and revert to the event collector for forensics and full record visibility, a DPI sensor can speed and facilitate access to traffic information by storing only the metadata (sender, receiver, device type, file type, etc.), and discarding irrelevant content, such as video content. In this way, the DPI sensor database provides high information resolution but uses only a fraction of the storage required for full packet capture (FPC). Indeed, the size of forensic data can be reduced by up to 150x compared to FPC. With the addition of traffic records from the DPI sensor, it becomes possible for security tools like SIEMs to reduce time to discovery and containment from weeks to days.
To be fully effective, a DPI probe needs to receive regular signature updates in order to recognize an extensive range of protocols (ideally, at least 3000), including new and outdated protocols, and identify devices/servers/VMs that they cross. Any irregular use of a protocol or use of an outdated protocol, for example, will immediately generate an alert allowing analysts to rapidly isolate the threat and protect network resources before a malware becomes active.
In addition, metadata extracted from traffic flows by the DPI sensor will provide a rich information feed that can be used to boost machine learning for User and Entity Behavior Analytics (UEBA) and Next Gen SIEM, strengthening threat analytics. This translates into more accurate alerts, shorter time-to-detection, and fewer false positives.
To find out more about DPI sensors for threat hunting and forensics, and in particular the Qosmos Probe DPI Sensor, please visit the following links:
- Deep Packet Inspection for Threat Hunting report:
https://www.cybersecurity-insiders.com/portfolio/deep-packet-inspection-threat-hunting-report/
- DPI Sensors for Cyber Threat Hunting – a 6 minute video overview on how DPI sensors can improve cyber threat hunting:
https://www.youtube.com/watch?v=yerjdbaJwSI
- Qosmos Probe website page:
https://www.qosmos.com/cybersecurity/dpi-sensor-for-threat-hunting/
- Qosmos Probe datasheet:
https://www.qosmos.com/wp-content/uploads/2018/10/Enea-Qosmos-SOC-DPI-Sensor-Datasheet-181003.pdf
About the Author
Erik Larsson is Senior Vice President of Marketing at Enea, where he drives product marketing, demand generation, branding and communication. Erik’s views on high-tech trends are regularly featured in articles, blog posts, webcasts, video interviews, and industry events.
About the Qosmos Division of Enea
The Qosmos Division of Enea is a pioneer in Deep Packet Inspection technology for physical, SDN and NFV architectures. Qosmos ixEngine®, the company’s DPI engine, is the de facto industry-standard for IP classification and metadata extraction. The Qosmos Probe is an award-winning, cost-effective DPI-based sensor, based on Qosmos ixEngine. It provides detailed visibility of network traffic, bringing new capabilities to SIEM and threat hunting platforms by pinpointing key data and improving the accuracy of threat detection. Security solution vendors and integrators use Qosmos to gain application visibility, accelerate product development and strengthen capabilities of new solutions. They benefit from Qosmos technical expertise in the development and integration of DPI technologies in their products and from continuous protocol signature updates, ensuring that their solutions always provide the most accurate network analysis available on the market. For more information on Qosmos technology and DPI in security solutions, please visit: http://www.qosmos.com/cybersecurity/overview/


















