

It’s always smart to do your research before buying and deploying any new business software or hardware. Don’t rush to embrace the “latest-and-greatest” technology because other companies are doing so. Yet Osterman Research has found that many IT security professionals are fast-tracking the implementation of Endpoint Detection and Response (EDR) solutions without fully understanding how they work or their potential impacts – both positive and negative – on security staff and their end-users.
That is one of the key conclusions of Osterman’s new report “The Critical Role of Endpoint Detection and Response” that examines the reasons a rapidly growing number of organizations are deploying (EDR) solutions to supplement their existing security defenses.
I recently co-hosted a webinar with Osterman Founder Michael Osterman to discuss the survey findings that serve as the report’s foundation, and it didn’t take long for the first red flag to appear.
Before I dive in, let’s consider what’s driving EDR’s popularity. The market for EDR solutions is growing at a rapid pace, from $238 million in 2015 to $1.54 billion in 2020. Why? Because the security landscape is radically different than at the turn of the century.
It used to be a CISO could sleep at night after implementing a firewall on the perimeter and an antivirus on all endpoint devices. But today there’s no rest for the weary, even after implementing dozens of different security products.
The attack surface has shifted with the rapid expansion of cloud computing and the destruction of the perimeter. Bad actors are more sophisticated, the consequences of a data breach are more severe, and a shortage in qualified security professionals exacerbates these problems for organizations across all industries.
EDR continuously monitors and records all endpoint activities and stores that information for future investigations along with some automated anomaly detection and IOC search capabilities. It’s a post-breach solution that provides the data your security analysts need to analyze how an attacker was able to penetrate your defenses and, hopefully, reduce the dwell time. This provides invaluable lessons into how to harden your security posture that traditional endpoint solutions cannot deliver.
The most popular reasons survey respondents gave for deploying EDR were its abilities to protect against fileless malware (72 percent), to improve post-breach remediation capabilities (67 percent), and to provide improved threat telemetry over conventional security solutions (67 percent).
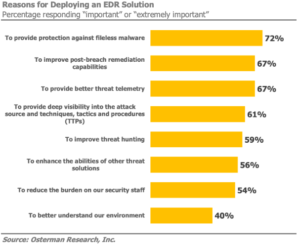
What surprised Michael and I was that more than half also expect to reduce the burden on their security staff. EDR solutions typically have just the opposite effect.
“EDR is not really a way to do that effectively because it does take some level of effort to understand and analyze the data an EDR solution provides,” said Osterman. “It’s not a set-it-and-forget-it solution, that’s not what it’s intended to do. That’s why we recommend that companies consider managed EDR solutions if they don’t have the internal expertise and budgets to properly manage an EDR solution.”
Osterman adds that it’s important to realize that EDR is not a replacement for most elements of your security infrastructure. It’s a supplement that will provide improved monitoring, insight and forensics capabilities. Yet many respondents have expectations of features and benefits that EDR cannot deliver.
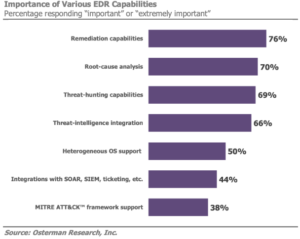

“If you’re looking for better protection, you’re buying (EDR) for the wrong reason,” added Osterman.
I think one of the questions we fielded from webinar attendees illustrates why EDR vendors need to do a better job of setting their customers’ expectations.
The question was “Is EDR a part of SIEM (security incident and event management) or compete with it?” The answer is “neither.” EDR can feed into SIEM for overall visibility, as SIEM can also draw visibility from network stack, authentication logs, and compliment with what’s happening on the endpoints with EDR.
We ended the webinar with Michael providing a number of questions any organization should pose to an EDR vendor before making a purchase, including:
- What are the additional staffing requirements to deploy and manage the solution on an ongoing basis?
- To what extent does the solution generate false positives?
- How much data will be generated by the EDR solution, and what impact will this have on performance, bandwidth and storage?
- To what extent is the threat detection and data analytics process automated, and can it help to prioritize alerts?
The full Osterman report not only analyzes the survey findings, it includes the entire list of 20 questions you should ask any EDR vendor. To download the full report, click here.
“We’re still in the very early stages of companies implementing EDR, it’s not a mature technology,” said Osterman. “The one point we need to keep stressing is that EDR is not a set-it-and-forget-it technology, you have to do something with the data it produces, and that requires investments in security labor to use effectively.”
To watch the entire webinar, click here.















