Deep Packet Inspection (DPI) technology, embedded in cybersecurity software, can enable faster, more accurate detection of network infiltration. DPI examines the data part of a packet as it passes an inspection point and alerts to any non-compliance protocols, viruses, spam, and malware. Leveraging DPI software to detect abnormal activity such as lateral movements can help organizations identify possible attacks before they compromise the network. This article explains how DPI can be used to detect network infiltration during the lateral movement phase, details different types of attack and describes the corresponding techniques used to identify the breach.
No organization is immune from malware attacks
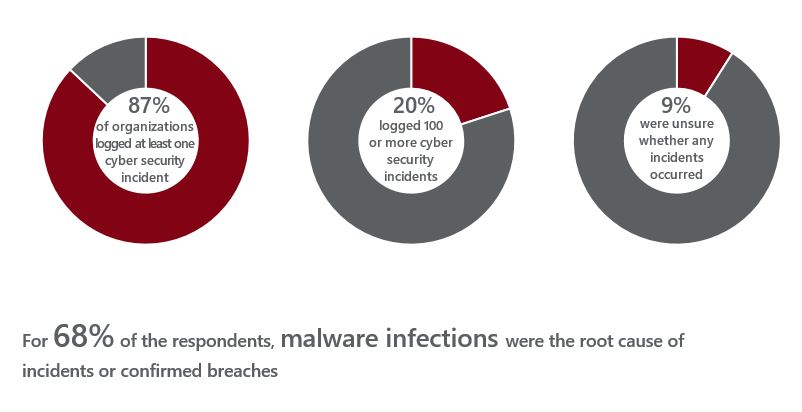
According to the 2017 Incident Response Survey by the SANS Institute, within the past 12 months:
In the same report, the top impediments facing Incident Response (IR) teams were given as:
These responses highlight two of today’s main challenges in keeping networks safe:
- Distinguishing potential threats from legitimate traffic requires the management and analysis of huge amounts of data often complicated by the high number of false positives.
- The time required to do this means that most current cybersecurity solutions are unable to defend networks against 0-day attacks.
Lateral movement generates network traffic
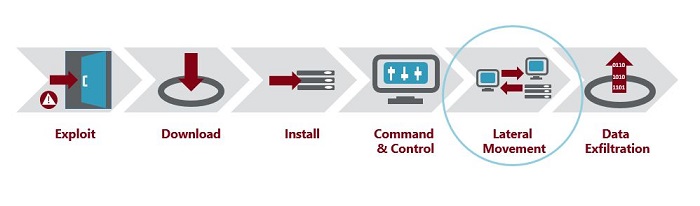
The Cyber Kill Chain
When malware penetrates a network through methods such as email phishing, a compromised external drive, an employee’s infected personal device, an IT misconfiguration or an unknown exploit, the attack typically evolves through the different stages of the cyber kill chain. It carries out early reconnaissance, creates a state of persistence, seeks access to the outside world through a Command & Control server, and then initiates a series of lateral movements (access to resources, propagation, privileges, etc.), until it reaches its final goal of data exfiltration, data destruction, or demand for ransom.
In a case study entitled “How to use cyber kill chain model to build cybersecurity?,” Ireneusz Tarnowski of the Wroclaw Centre for Networking and Supercomputing, explains that depending on the quality of the preparation for an attack, intrusion may take only a few seconds, but if the attack is not noticed, it can be hidden and intrude the infrastructure of the victim over a long period of time, extending up to several months.
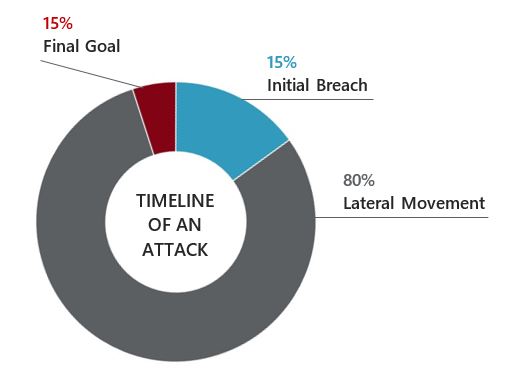
Estimated Attack Timeline
During the lateral movements phase, an attack generates specific types of network traffic and it is here that it becomes vulnerable to detection by specialized DPI technology. DPI software monitors network traffic, analyzing flows in real-time, using an extensive library of protocol and application metadata to distinguish between normal and abnormal activity. As a result, lateral movements are rapidly identified and the resulting intelligence is fed to the system’s cybersecurity software, which is then able to locate the malware and immediately stop the propagation of the attack.
Since lateral movement typically accounts for the longest period in an attack timeline, it allows DPI to accurately detect suspicious network-based activity and alert the security system to initiate action before harm is done.
Typical techniques used by malware during lateral movement
For host-based techniques, DPI is of limited added value in detecting the threat:
- Token stealing / credential stealing, Pass-the-hash
- PowerShell
- Network sniffing
However, for network-based techniques, DPI is highly effective in detecting the lateral movement
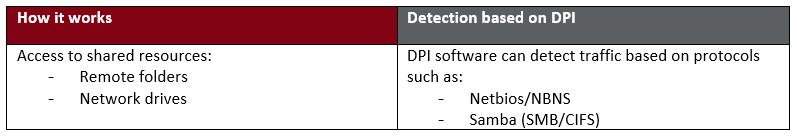
- File shares
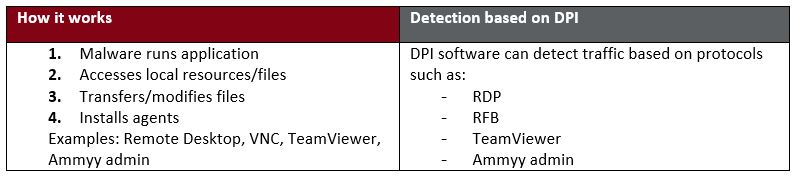
- Remote desktop, VNC, TeamViewer, Ammyy Admin
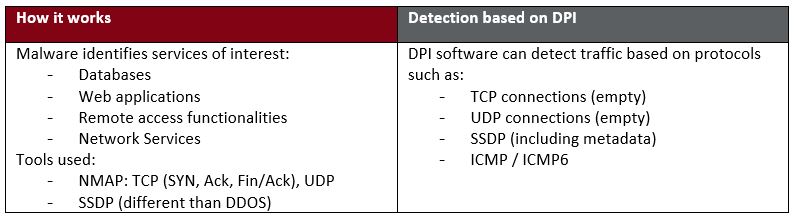
- Port scan
- Windows Management Instrumentation (WMI)
- Active directory & admin shares
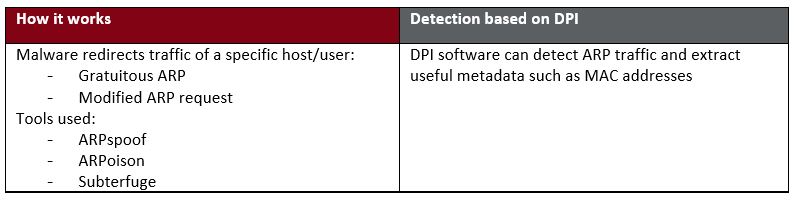
- ARP spoofing
How DPI detects network-based lateral movement
Lateral Movement using File Shares
Lateral Movement using Remote Resources
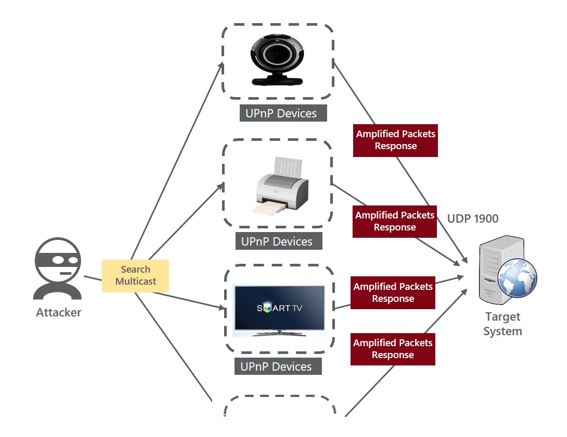
Lateral Movement using Services/Servers Scan
SSDP Flood – DPI software can detect traffic based on SSDP protocols
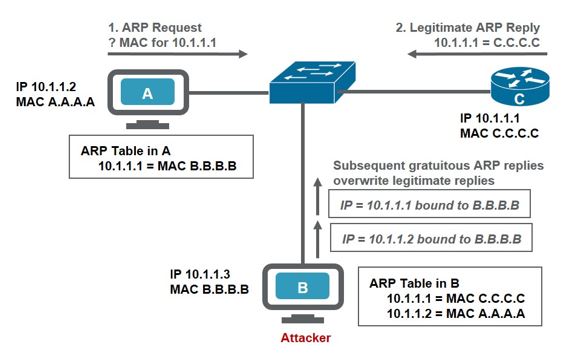
Lateral Movement using ARP spoofing/poisoning (man-in-the-middle)
ARP spoofing attacks and ARP cache poisoning can occur because ARP allows a gratuitous reply from a host even if an ARP request was not received. After the attack, all traffic from the device under attack flows through the attacker’s computer and then to the router, switch, or host.
Conclusion
DPI software is highly effective in accurately detecting network-based lateral movement, while allowing rapid containment of attacks and remediation. The protocol information and metadata can be used to improve the results of user behavior analysis and machine learning, and to enable mitigation at each stage of the kill chain, improving the effectiveness of security solutions.
An example of DPI software that can be used in the detection of lateral movement is Enea’s Qosmos ixEngine®. It is a Software Development Kit enabling DPI capabilities to be embedded in cybersecurity solutions. The software recognizes more than 3,000 protocols, including key network protocols such as SMB, DHCP, and Industrial Control System (ICS) protocols. Qosmos ixEngine can also extract additional protocol information in the form of metadata (recognizing up to 4500), further improving the effectiveness of threat detection.
For more information, please visit: http://www.qosmos.com/cybersecurity/lateral-movement-detection/
by Erik Larsson, SVP Marketing, Enea and Belgacem Hlali, Senior Global Technical Account Manager, Qosmos Division, Enea
About the Authors
Erik Larsson is Senior Vice President of Marketing at Enea, where he drives product marketing, demand generation, branding and communication. Erik’s views on high-tech trends are regularly featured in articles, blog posts, webcasts, video interviews, and industry events.
Belgacem Hlali is Senior Global Technical Account Manager at the Qosmos Division of Enea. He has over 17 years’ experience in the architecture, design and development of IP technologies with specific expertise in Deep Packet Inspection, Networking and IP Security.
About the Qosmos Division of Enea
The Qosmos Division of Enea is a pioneer in Deep Packet Inspection technology for physical, SDN and NFV architectures. Qosmos ixEngine®, the company’s DPI engine, is the de facto industry-standard for IP classification and metadata extraction. Security solution vendors and integrators use Qosmos to gain application visibility, accelerate product development and strengthen capabilities of new solutions. They benefit from Qosmos technical expertise in the development and integration of DPI technologies in their products and from continuous protocol signature updates, ensuring that their solutions always provide the most accurate network analysis available on the market. For more information on Qosmos technology and DPI in security solutions, please visit: http://www.qosmos.com/cybersecurity/overview/