

As cyber attacks become increasingly sophisticated, traditional solutions based on known signatures often fall short allowing new malware and zero day attacks to penetrate networks without being identified.
A virus, for example, might enter a system as an email attachment. Once it becomes active, it will begin system reconnaissance, seeking access to resources and privileges, and try to contact external servers. It might also carry out propagation activities or try to exfiltrate or destroy data. Without continuous and detailed analysis of the network traffic, it will be nearly impossible to detect these activities before damage occurs. In addition, even with constant and detailed network analysis, if the security solution is unable to recognize a wide enough range of protocols and applications, sophisticated malware that uses recent, uncommon or outdated protocols will easily be able to move around a network unseen. It is therefore important for security solutions to have both continuous analysis of network traffic and extensive recognition of protocols.
How do DPI sensors strengthen threat hunting?
Deep Packet Inspection (DPI) sensors represent a new form factor that leverages the granular visibility of DPI to complement existing security tech stacks and significantly strengthen threat hunting capabilities. DPI is a proven technology that is already widely used in cybersecurity to detect and mitigate threats. It is often embedded in NG firewalls, UTM, secure gateways, and different types of threat analysis tools to ensure rapid and reliable detection of malware attempts and security breaches.
Used as a complement to traditional network security solutions, the DPI sensor is an expert tool for network forensics and threat hunting. It streamlines investigations and improves time-to-detection by capturing and analyzing 100% of traffic in real-time, including both traffic shape (volumes, origin & destination, device type/VM, etc…) and content (attachments, encapsulated traffic, etc…). Through regular signature updates, DPI sensors can recognize an extensive range of protocols, including new and outdated protocols, and identify devices/servers/VMs that they cross. When an anomaly is detected, such as irregular use of a protocol or use of an outdated protocol, an alert is generated. Hunters can then isolate the threat and protect network resources before the virus becomes active.
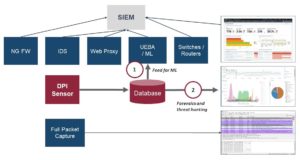
In addition, the metadata extracted from traffic flows by the DPI sensor provides a rich information feed that can be used to boost machine learning for User and Entity Behavior Analytics (UEBA) and Next Gen SIEM, strengthening threat analytics. This translates into more accurate alerts, shorter time-to-detection, and fewer false positives.
The DPI sensor stores the traffic information it captures in a database where it can be accessed rapidly and easily for query and visualization. The sensor provides high information resolution using a fraction of the storage required for full packet capture because it only requires traffic metadata (sender, receiver, device type, file type, etc.), discarding irrelevant content, such as encrypted data or video content.
How are DPI sensors integrated in a threat hunting environment?
DPI sensors are part of the global architecture of a Security Operations Center (SOC), and can be seamlessly integrated with other parts of a threat intelligence technology stack: SIEM, IDS, Full Packet Capture, etc. As an example, information from the DPI sensor can improve IDS rules, which means fewer false positives.
Sensors can be deployed and activated on-demand, as physical resources or virtual machines, with minimal impact on performance – typically less than 2 to 3% of CPU.
The following figure shows a critical infrastructure SOC equipped with a DPI sensor.

Conclusion
While all network security solutions include some kind of traffic monitoring function, their effectiveness is limited by the amount of traffic they can analyze in real-time, the number of protocols they recognize (usually known signatures available at the time of deployment) and their ability to provide granular visibility of network activity. The addition of a DPI-based dedicated probe or sensor that can analyze and classify traffic in real-time, recognizing very large numbers of protocols and extracting specific kinds of metadata, can significantly improve the ability of existing security solutions to detect malware and contain attacks before damage is done. They are a simple and cost effective way of boosting system security.
Experience with DPI sensor deployments shows the following benefits when used as a complement to traditional network security solutions:
• Improved threat hunting capabilities thanks to detailed real-time traffic information
• Fewer false positives when using information from the DPI sensor to improve IDS rules
• Reduced size of forensic data: up to 150x compared to Full Packet Capture
More information:
Report: Deep Packet Inspection for Threat Hunting
Published by Cybersecurity Insiders for Enea’s Qosmos Division, the report summarizes the findings and conclusions of a survey among cybersecurity professionals.
https://www.cybersecurity-insiders.com/portfolio/deep-packet-inspection-threat-hunting-report/
Webinar: How to Strengthen Threat Hunting with DPI Sensors
Watch this on-demand webinar to hear cybersecurity experts discuss the findings of the survey on DPI sensors, how to transparently integrate DPI sensors within a SOC security stack and examples of attack scenarios that can only be detected with DPI sensors.
https://www.cybersecurity-insiders.com/how-to-strengthen-threat-hunting-with-dpi-sensors/
About the Author
Sebastien Synold is Product Manager at the Qosmos Division of Enea. He has extensive experience in IP technologies, specializing in Deep Packet Inspection and networking applications. He is particularly interested in innovation technologies and previous responsibilities have included management of SDN and NFV product lines. He is currently in charge of the new DPI Probe product line which brings security analysts full visibility into their virtual or physical data center traffic.
To contact the author or for more information: http://qosmos.com/company/contact-us/
About the Qosmos Division of Enea
The Qosmos Division of Enea is a pioneer in Deep Packet Inspection technology for physical, SDN and NFV architectures. Security solution vendors and integrators use Qosmos to gain application visibility, accelerate product development and strengthen capabilities of new solutions. They benefit from Qosmos technical expertise in the development and integration of DPI technologies in their products and from continuous protocol signature updates, ensuring that their solutions always provide the most accurate network analysis available on the market.
Enea’s Qosmos Probe is a DPI sensor that embeds the market-leading DPI engine, Qosmos ixEngine®. It leverages years of experience from the most demanding environments, including cyber defense. Used by large SOCs operated by high-end MSSPs and Managed Detection & Response (MDR) service providers, it has become a key technology for advanced threat hunting.
Key characteristics include:
- Comprehensive analysis of network traffic, including content verification (file format compliant with real content, protocol characteristics instead of port-identification-only, encapsulated protocols, etc.), encrypted traffic autopsy, etc.
- Scalable throughput up to hundreds of Gbps
- Real-time insights that trigger immediate alarms and threat hunting actions
- Long term historical data storage based on traffic metadata – typically 1 year or more (compared to Full Packet Capture which is often limited to as little as 1 week)
- 3100+ protocols analyzed
For more information on the Qosmos Probe DPI sensor:
https://qosmos.com/cybersecurity/dpi-sensor-for-threat-hunting/















